.DLL Hijacking Roundup!
 Friday, August 27, 2010 at 11:02AM
Friday, August 27, 2010 at 11:02AM So welcome to the madness of .dll hijacking...
Lets recap everything that has happened thus far.
The current 2010 madness started with ACROS Security when they announced on 8/18/2010 about "binary planting" vulnerability in Apple iTunes for Windows.
HD Moore from Rapid7 said on twitter "The cat is out of the bag, this issue affects about 40 different apps, including the Windows shell" linking to the ACROS advisory. The ACROS advisory hinted that it was more then just iTunes. HD promised that the following Monday that he would announce more information.
This was going to be a long weekend for some. However for me, "Its the end of the world as we know it... and I feel fine." I went out of town to the beach. I had a great time and I recommend the Marriott Hutchinson Island in Florida. This is not related to the story.
@jcran sensing the world was going to end took a trip through the Midwest under the excuse of a bachelor party. This will be the basis for the movie Hangover 2. This maybe related but we need to wait to see how the movie turns out.
Ok back to the .DLL! Monday rolls around. HD Moore releases a post on Rapid7's Security Blog titled "Application DLL Load Hijacking."
In his post, he notes that this has been around since 2000. It was originally noted by Georgi Guninski on Sep. 18, 2000 and links to a Microsoft MSDN article. He also notes that earlier this year, Taeho Kwon and Zhendong Su published a paper titled Automatic Detection of Vulnerable Dynamic Component Loadings. Since the "cat was out of the bag" HD pushed a generic exploit module to the Metasploit Framework.
So how do I protect myself?
HD also released an audit kit that can be used to identify naughty applications. <~ Download this right now!
Microsoft as helpful as always issued their Security Advisory and Support. This issue can not be fixed by Microsoft alone. It is up to the individual application programmers. Since this is not a buffer overflow/stack smash, there is not a simple fix. A fix could break other applications!
Microsoft has offered guidance to developers here.
Dave Marcus from McAfee has released a PodCast on it. It is also available on iTunes.
Ok... So how hard is this to exploit? Do I need to be an evil genius?
Hell NO! Let's get to some fun stuff... our first video comes from David Kennedy aka dave_rel1k.
Another great video is from Offensive Security. This one has awesome music by DualCore.
If this seems too technical for you, you can get a trial copy of Metasploit Express. This application has the exploit ready to go with a point, click, pwn interface.
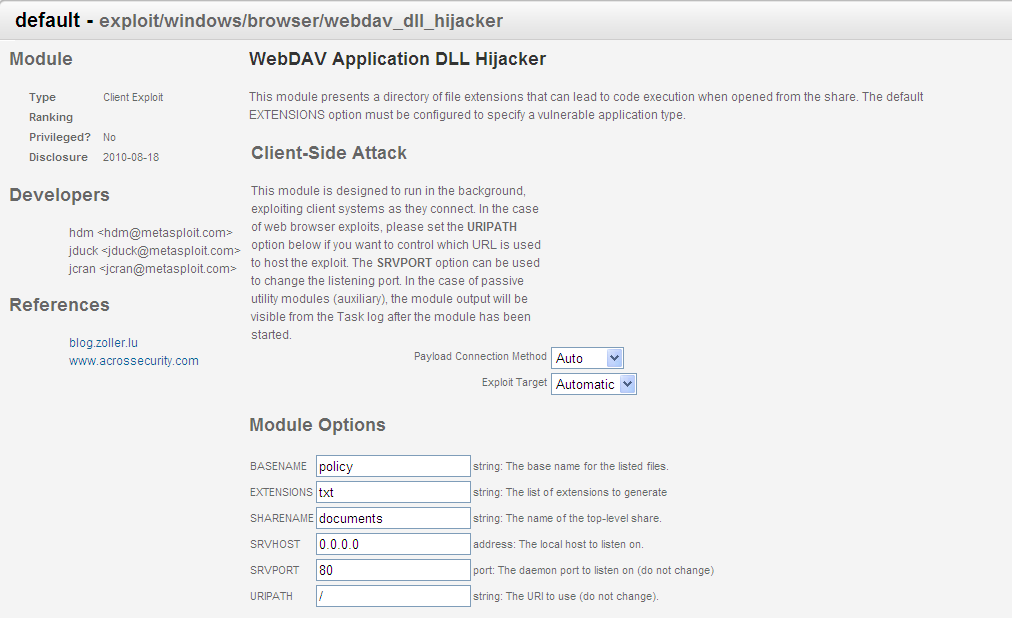
Ok... So where do I find a list of applications that are vulnerable?
I recommend going to the following 3 sites.
DLL Hijacking (KB 2269637) – the unofficial list
DLL Hijacking – Vulnerable Applications- Exploit DB
VUPEN Security Advisories- Insecure Library Loading
You should also test your own system with HD Moore's audit kit.
It has been an interesting week in the world of information security. I can't wait to see what next week brings!
