Client Side Attacks with Metasploit Express
 Wednesday, August 18, 2010 at 3:55PM
Wednesday, August 18, 2010 at 3:55PM Today the team over at Rapid7 updated Metasploit Express today.
This inspired me to play around with the application and checked out the modules.
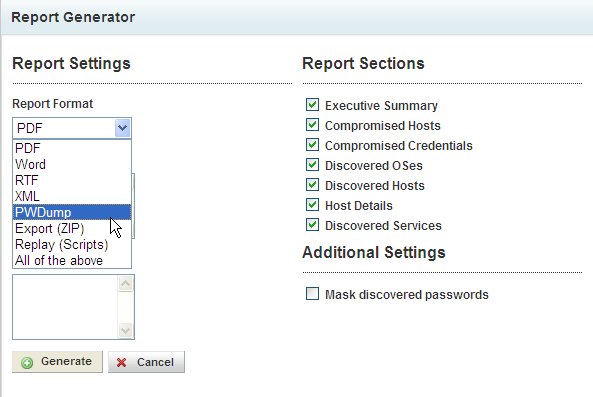
I know some of the fun of Metasploit is Client Side Attacks. I figured I would test one of the modules out. The tough part was choosing which module to use.
Lucky for me, Metasploit rates the exploits and I found one rated 5 starts. Signed Applet Social Engineering Code Exec.
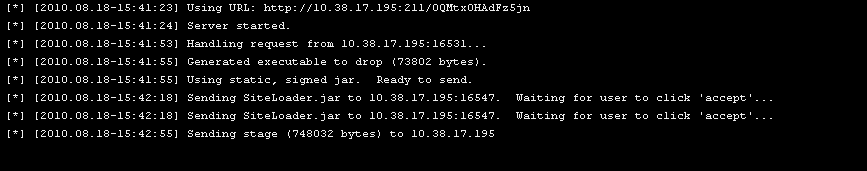
Time to fire up the browser and go to the link the exploit was waiting on. It looks like a pop up... do I click?

and the trap has been set...
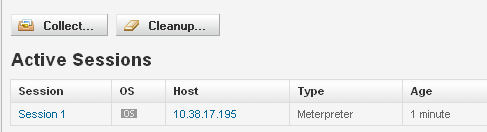
The code executed and showed me I have 1 session loaded.

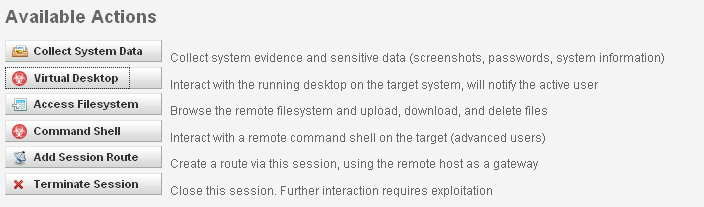
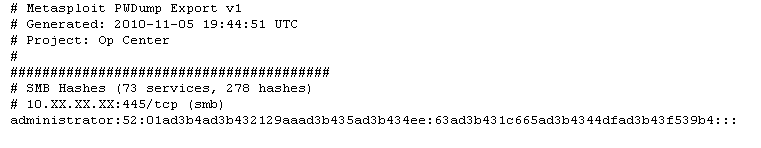
Now normally when using the framework, I would be loading extensions to get some hashes and other goodies.
This time I hit a button. Click. Metasploit Express returned a picture of my desktop and my password hashes.

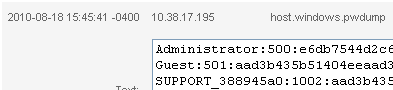
You can get a 7 day demo of the application over at http://www.rapid7.com/contact/metasploit-express-contact.jsp
To see the updates released today click here: http://www.metasploit.com/redmine/projects/pro/wiki/Updates_341

Reader Comments