Check out V.3.6 Updated Features Here
http://www.n00bz.net/blog/2011/3/8/metasploit-36-review.html
Metasploit Pro- Review
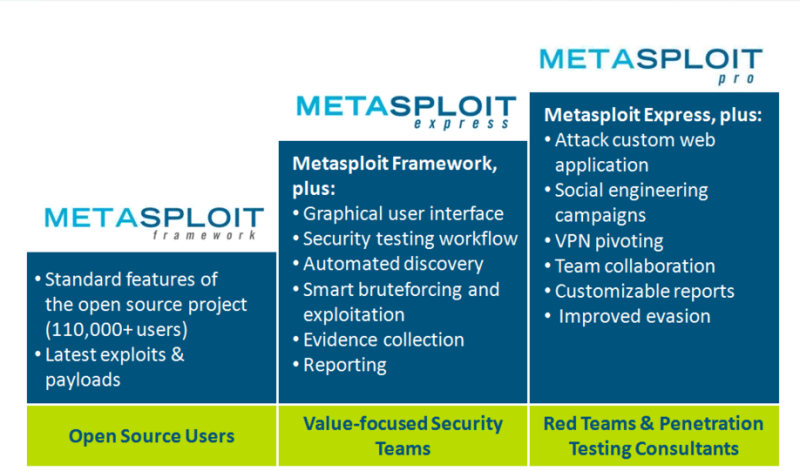
Last year, HackMiami had a Pwn-Off in which Metasploit Express was declared the winner with 4.5/5 stars. In comparing Express with Core, it was noted that, “Core includes not only Network Testing, but Web and Client Side/Phishing attack vectors as well. You will pay for these features however.”
At BlackHat/Defcon, Rapid7 announced that it would take it’s offerings to the next level along with a video. http://www.youtube.com/watch?v=jXGF9Giz7No
Behold, Metasploit Pro!
Metasploit Pro includes all the features of Express along with Web Attacks, Social Engineering, VPN pivoting as well as Team Collaboration.
Team Collaboration and VPN Taps
@rodsoto and myself decided to test out the features of Pro. The first thing we tested was Team Collaboration. Rod was in Miami and I was in Orlando. We used a local company, NewServers.com to create a cloud instance of Metasploit Pro.
First thing we notice is that the menu bar has some updates. Campaigns and Web Apps are 2 new attack vectors added to the application.
Using the Hosts tab, Rod scanned our 1st target.
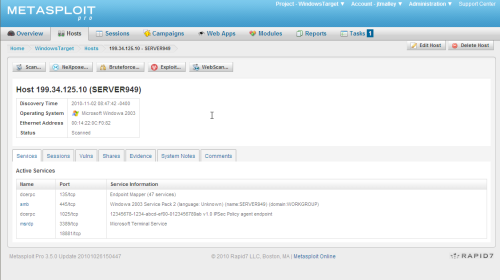
Express had Bruteforce and Exploit, but Pro adds a new button to the top of the Host Page, WebScan.
Selecting the Web Scan button launches the module sharing the knowledge obtained in the scan.
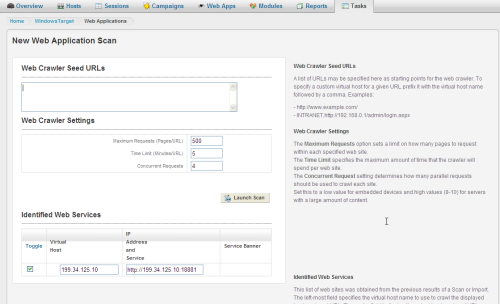
The Web Application Scan crawls the site looking for pages and forms.
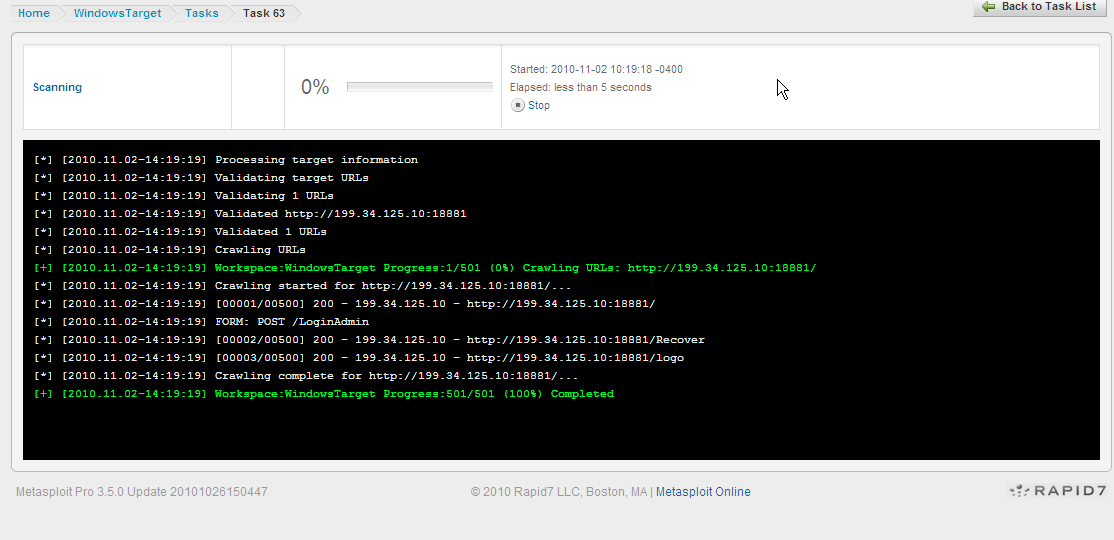
Once identified, the user can Audit the forms identified. The tool will look for SQL injections, XSS, as well as RFI. More on this later...
The scan returned that no web vulnerabilities were identified on the server. At this time Rod handed off the project to me.
Browsing to the site, I saw the following page. Integard Pro.
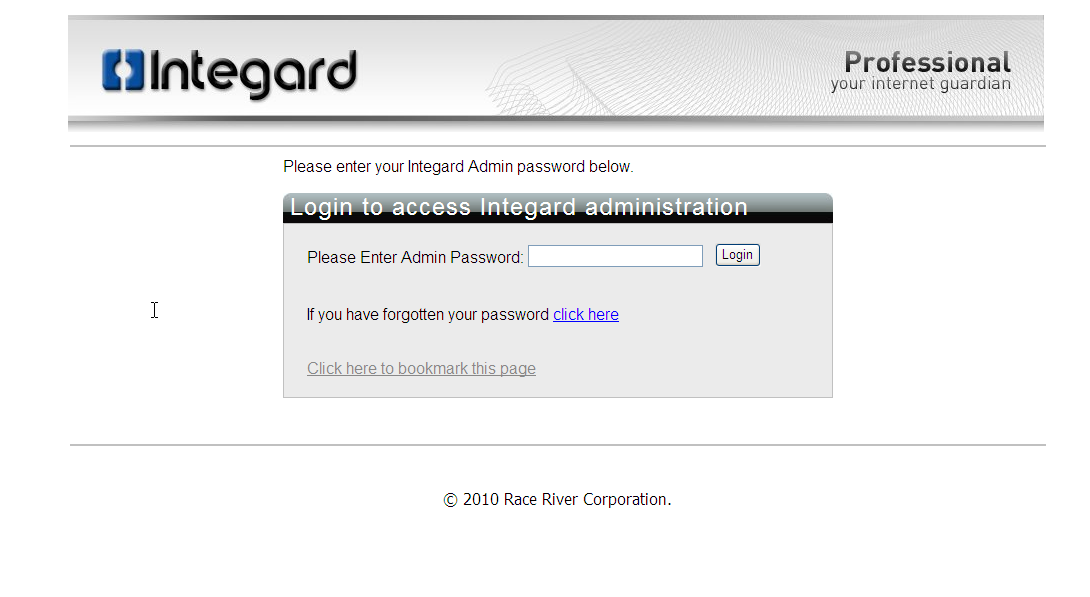 Heading over to the CORELAN Team’s site I saw the advisory. http://www.corelan.be:8800/advisories.php?id=CORELAN-10-061 and found the Exploit in the Modules section.
Heading over to the CORELAN Team’s site I saw the advisory. http://www.corelan.be:8800/advisories.php?id=CORELAN-10-061 and found the Exploit in the Modules section.
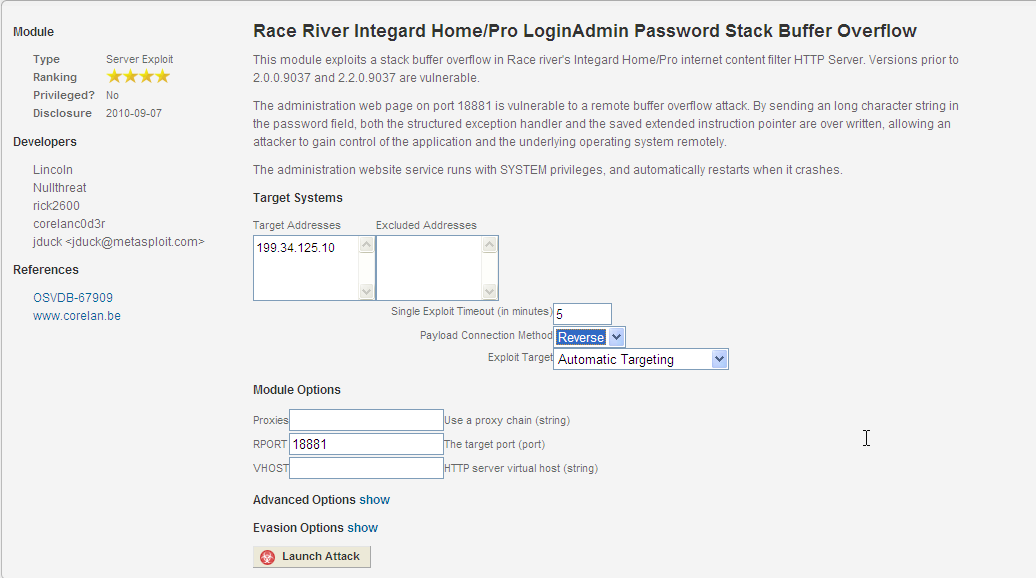
Launching the exploit I was rewarded with a Session.
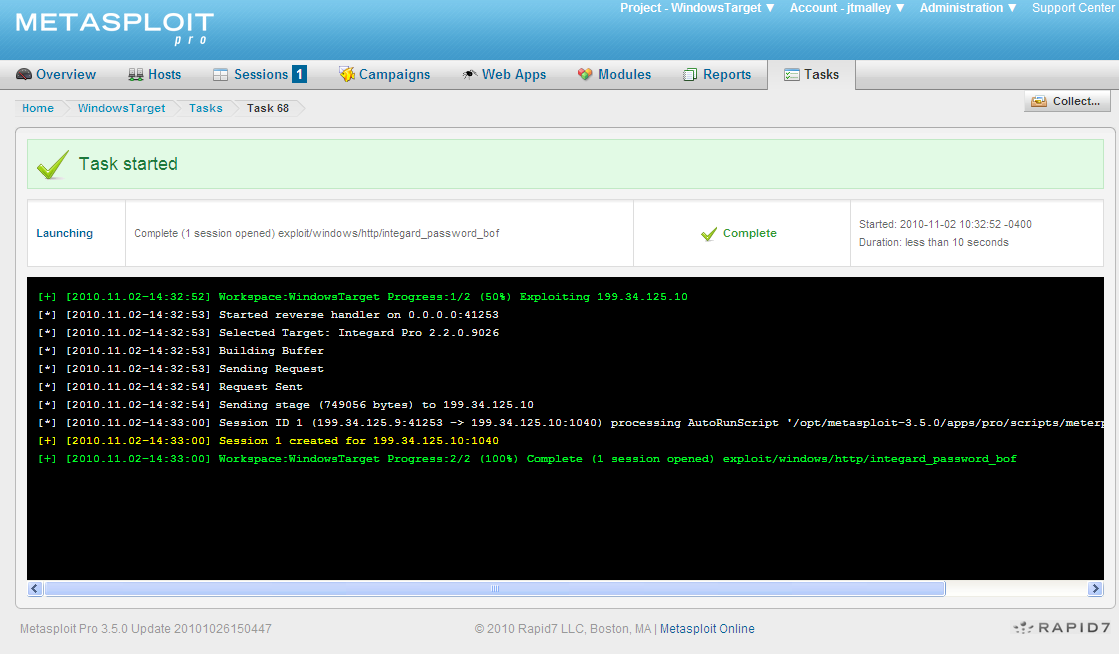
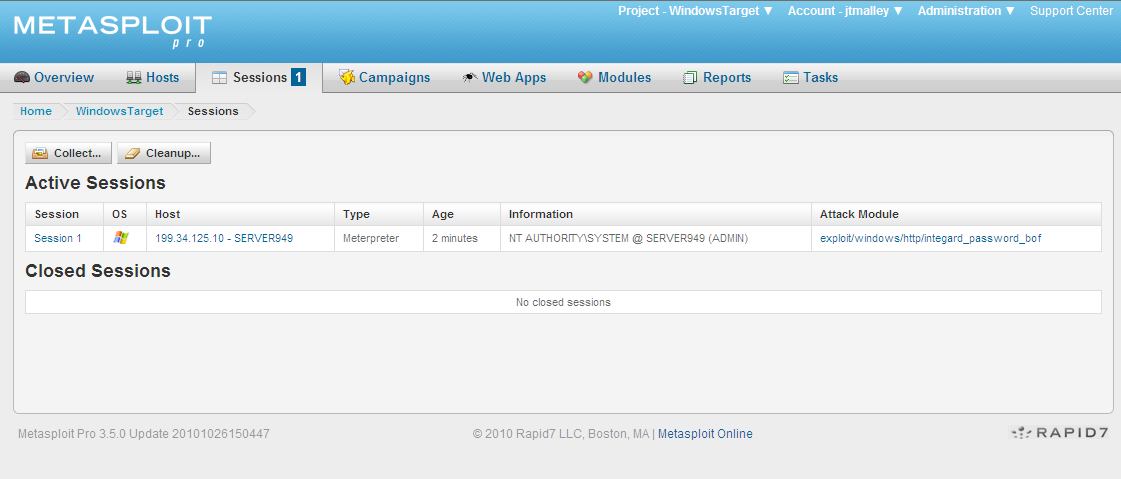
New to the Available Actions on the Session screen is VPN Pivot. Express allows a Proxy Pivot, creating a gateway through the compromised machine and allows you to scan further into the network. Metasploit Pro allows the user to create a VPN gateway on your target machine to which you have an encrypted layer 2 connection. VPN pivoting creates a virtual Ethernet adapter on the Metasploit Pro machine that enables you to route ANY traffic through the target. The keyword is ANY! If you have a special tool you purchased or custom tool that you wrote, you can use it. This virtual tap combined with all the attack vectors in Metasploit Pro makes this a very powerful feature.
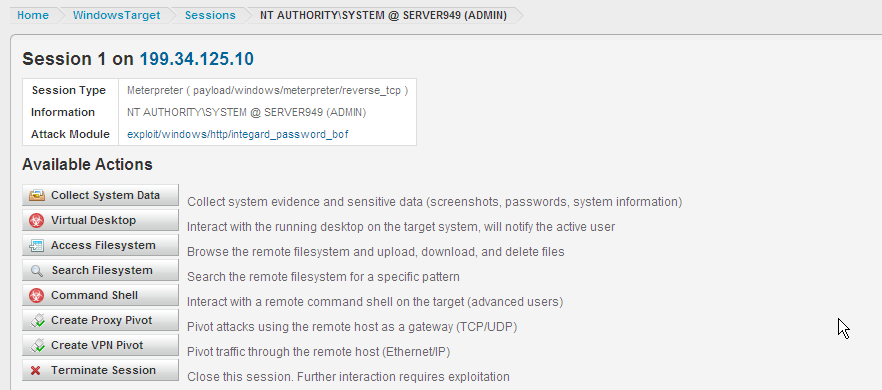
We had a second target machine set up in our environment. This was out on the internet for our testing, however if it was behind a firewall our network tap would have made it 100% available.
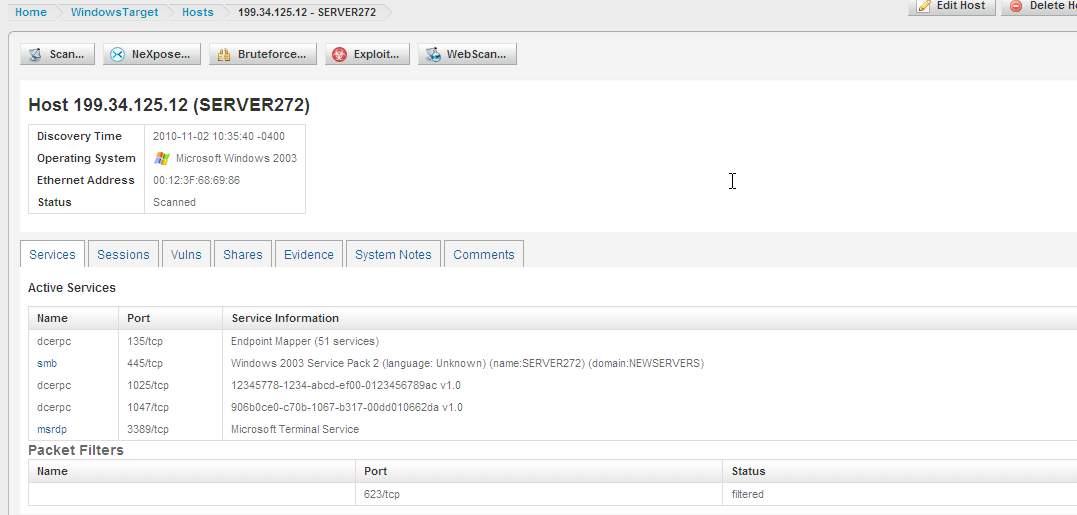
Passing the Hash we collected is simple. Hashes were collected when we Looted the first server.
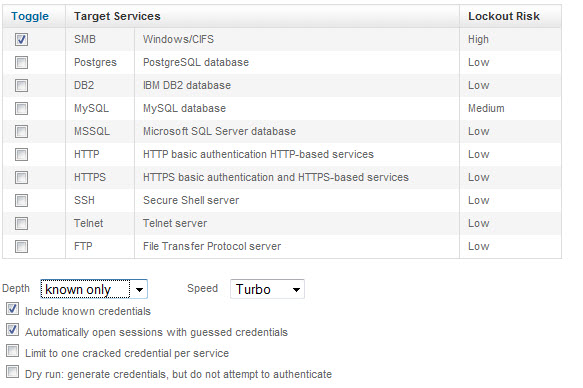
Let's see if we can pass the hashes to the second server. To pass the hash using Pro, Select the Bruteforcing attack and under depth select known only.
We were able to authenticate to the second server since a common username/password was used.
I passed the project back to Rod to exploit the 2nd Server.
He was able to search the file system and found a folder called TopSecret.
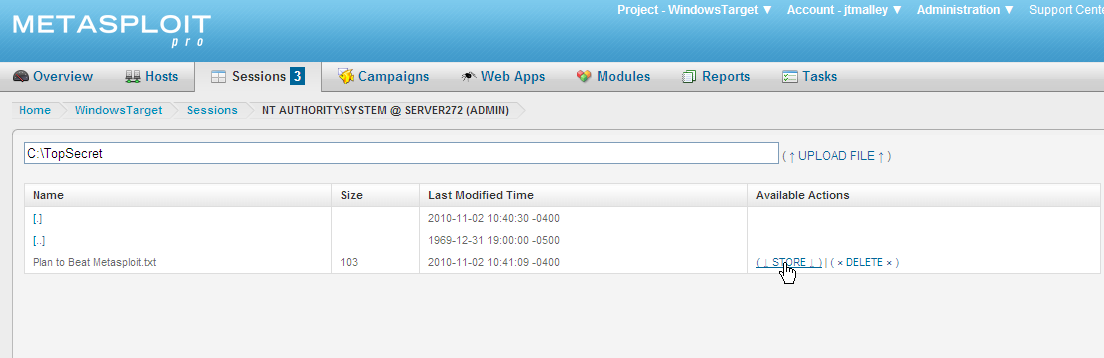
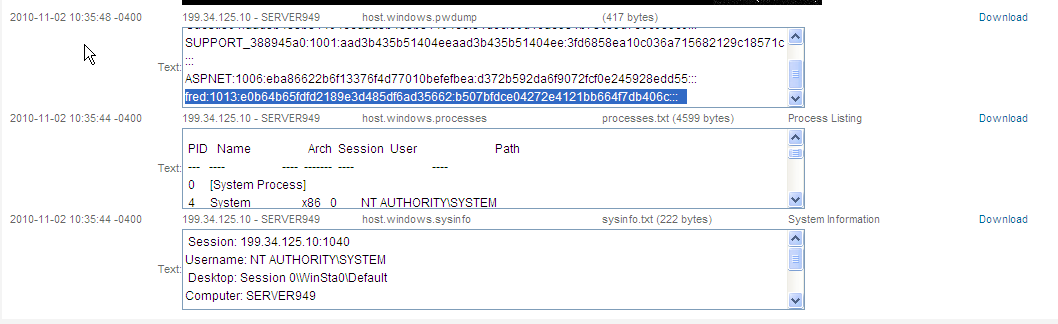
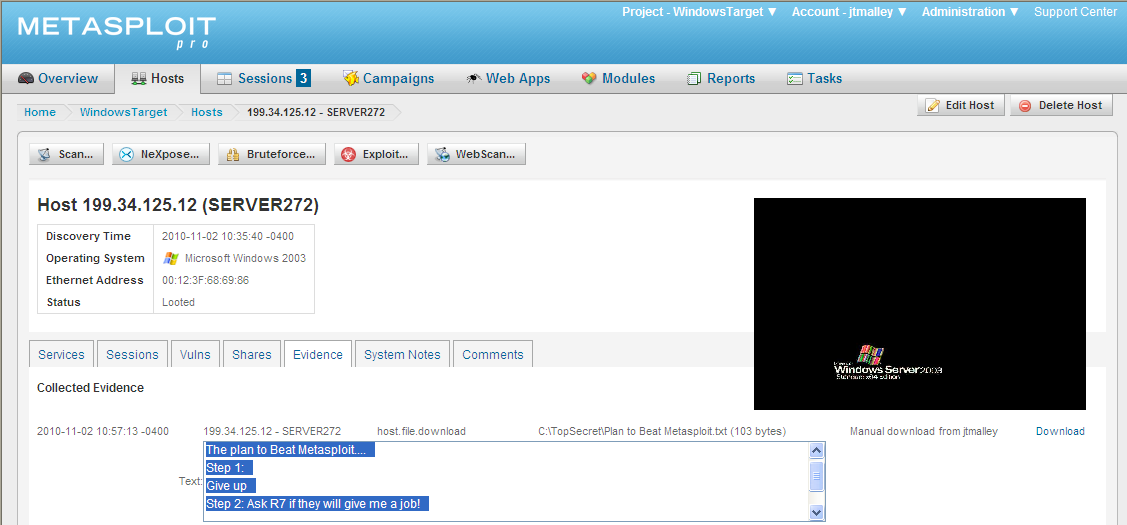
He emailed me to check the Evidence of Server272. I logged into the Metasploit Pro server and found the Evidence he collected.
Web Application Attacks
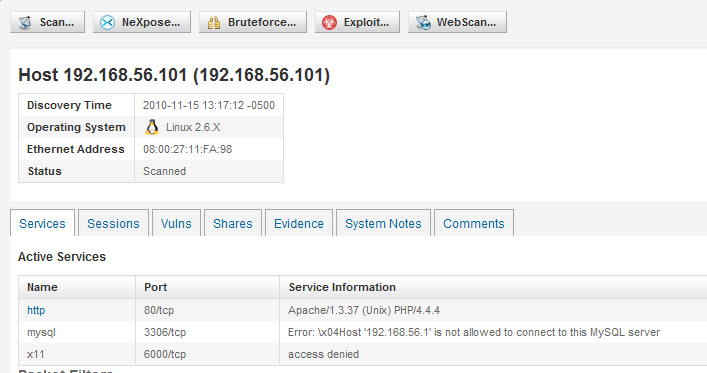
I decided to test the Web Application Attacks Module to further show how it works. I fired up DVL as a target. DVL has several web applications that are insecure. A perfect test of the Web Attack modules of Metasploit Pro.
First thing I did was scan the host and the scan identified port 80 was open.
Clicking WebScan passes all the information over to the Web Scanning Module.
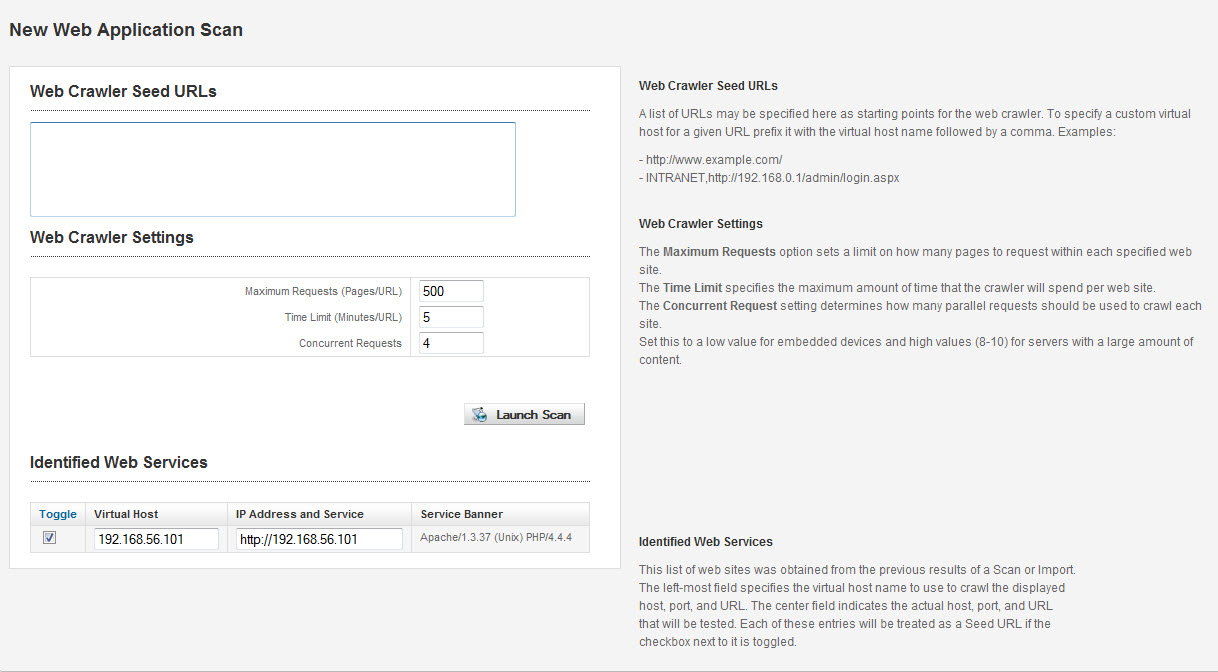
Launch the scan and the application does the rest. It quickly found several vulnerabilities.
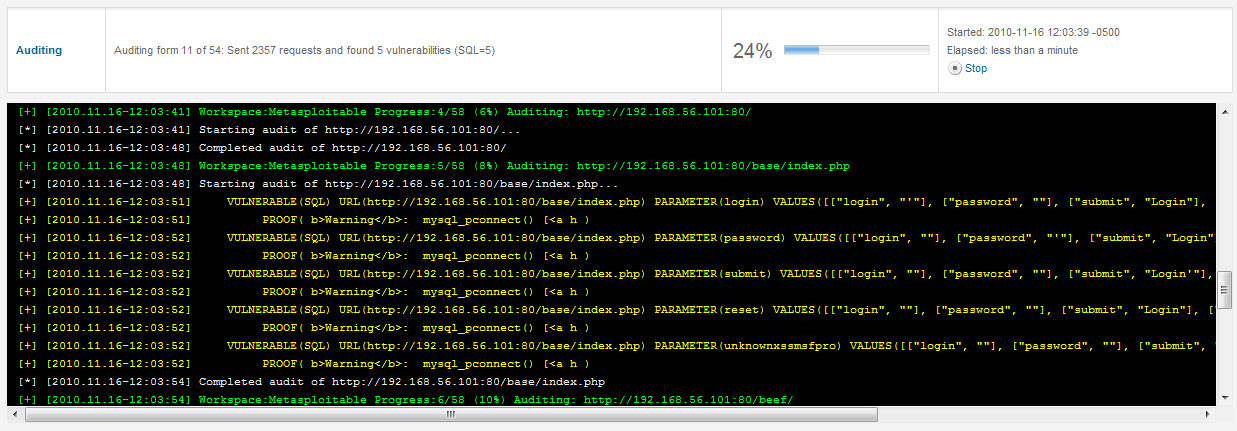
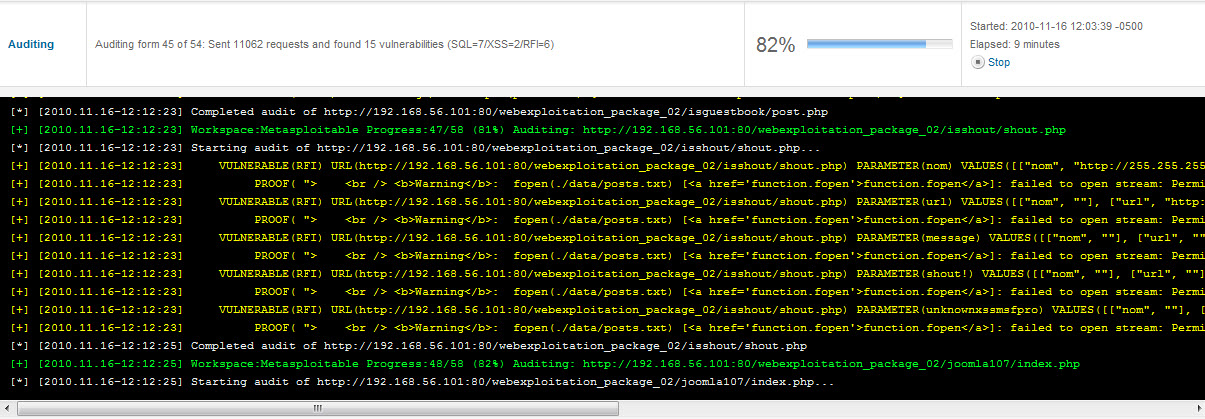
Once the scan is completed, a list of findings is presented.
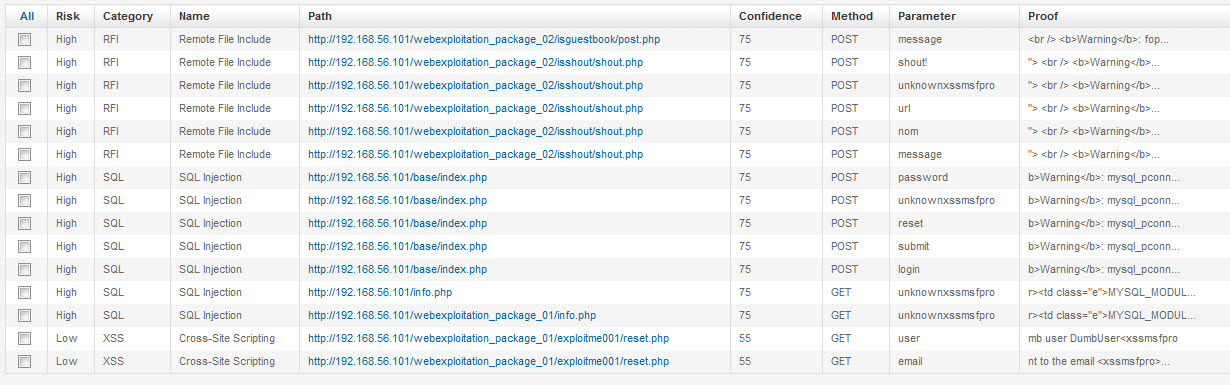
Metasploit Pro allows you to see the fill information of the finding as well as replay the attack.
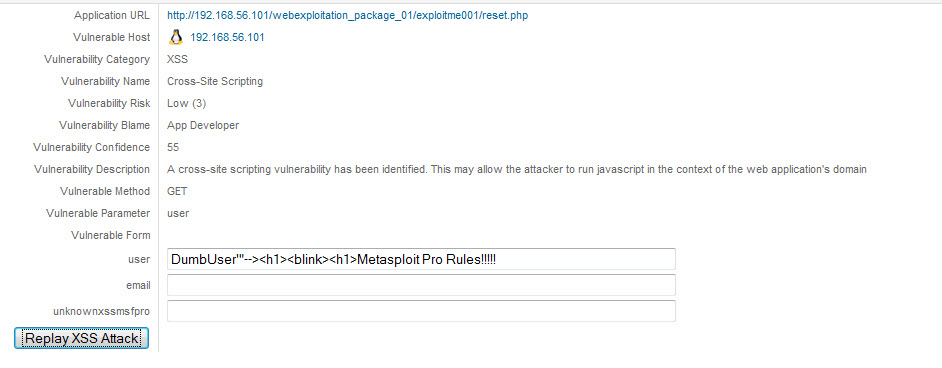
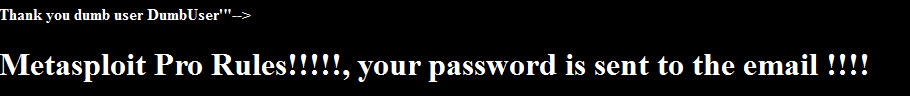
This is available for SQL attacks as well.
When SQL Injections and XSS are identified, the tool gives you the ability to dive deeper.
When a problem like RFI is identified, thanks to Meterpreter a la PHP http://blog.metasploit.com/2010/06/meterpreter-for-pwned-home-pages.html one can take control of an external web server and create a VPN tap and... I will leave it up to your imagination.
Campaigns- Social Engineering
Social Engineering is the new attack vector. Metasploit Pro offers Social Engineering made easy. You can use Web Campaigns, Email, or my favorite, USB Drive.
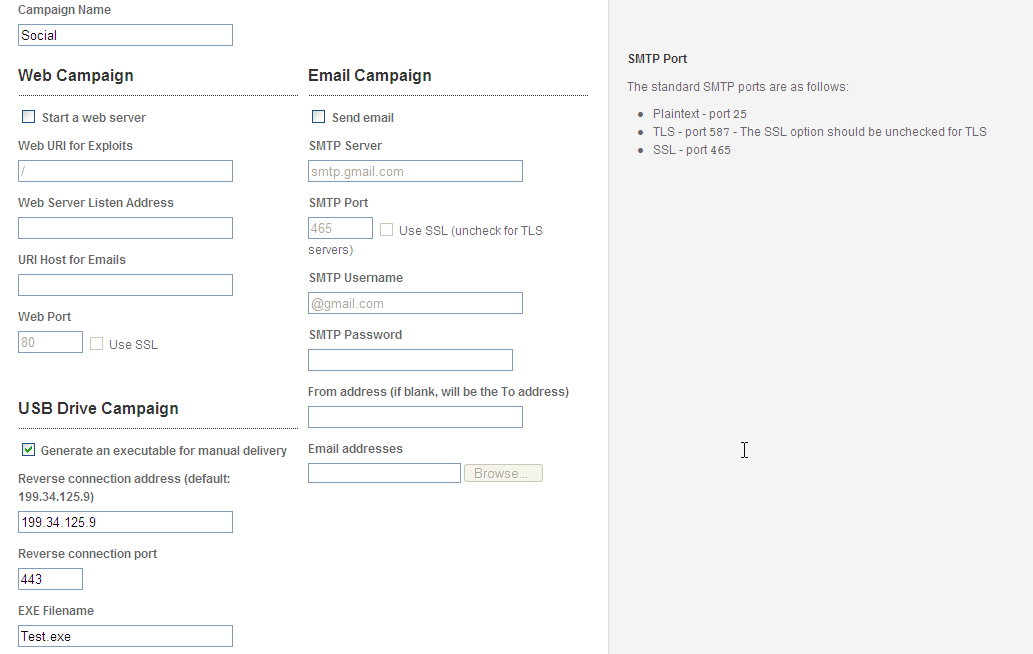
If you want to launch a Web Campaign, Setting up the Web Template is a breeze. A great trick is to go to a real site and copy the HTML Source.
Note: If the website that you copy & paste from uses relative links, remember to set the base href attribute & force the page to use the original site’s files to render. — more information here: http://www.w3schools.com/tags/tag_base.asp
You select your Exploit Settings from a Dropdown or you can use Browser Autopwn.
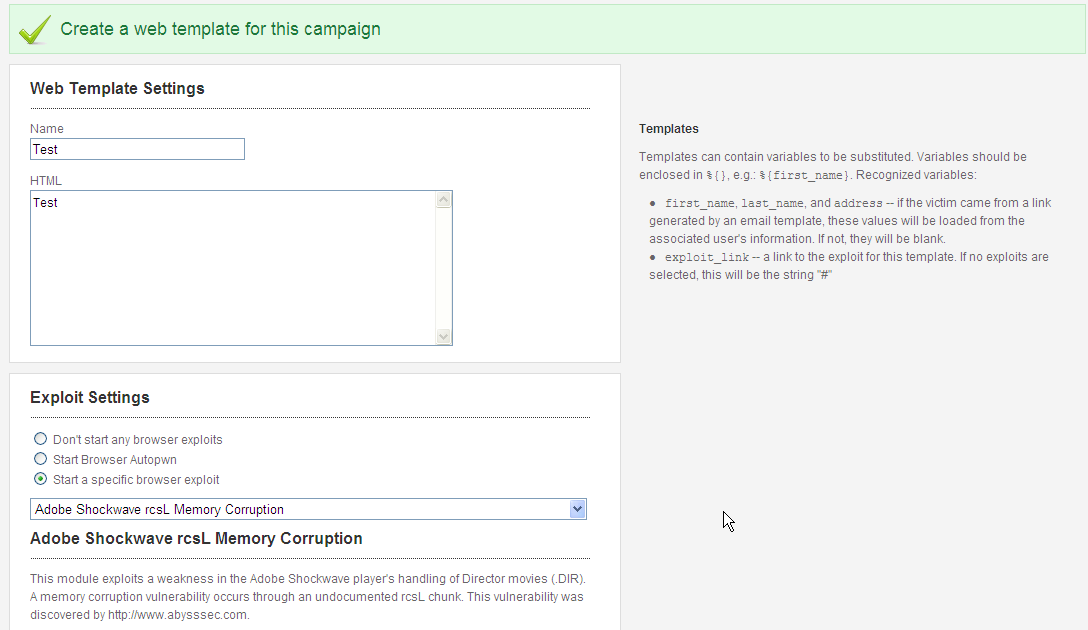
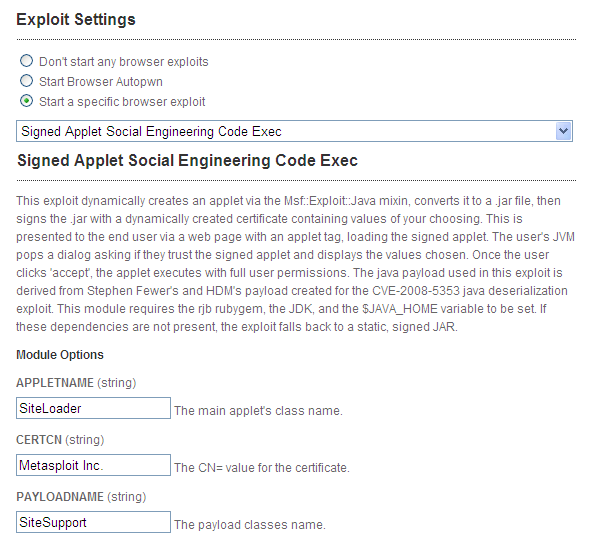
My favorite choice is the Signed Applet Social Engineering Code Exec.
When the victim browses to your evil site, they get a pop up.
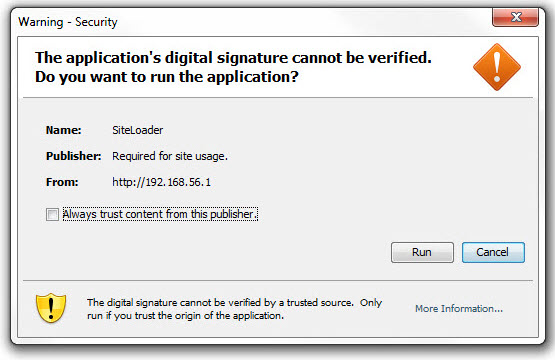
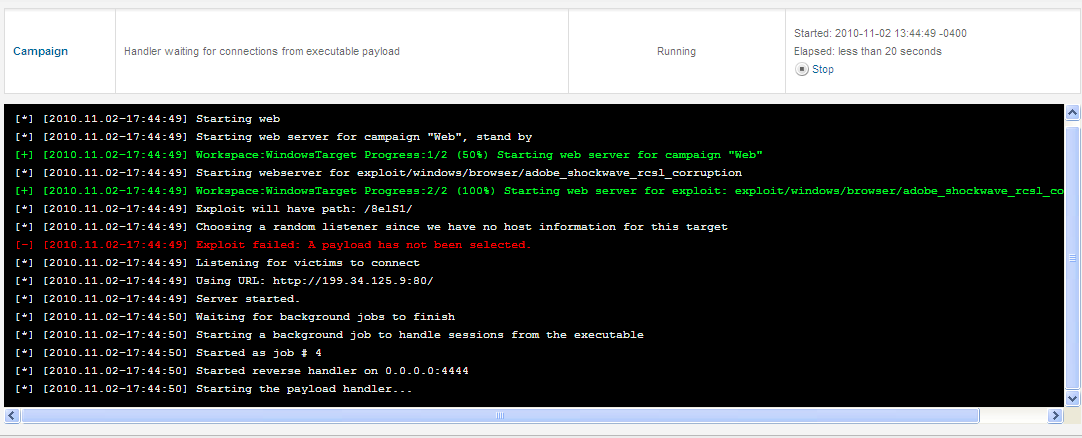
When they click Run/Yes…. you have a session.
Matt over at Practical Pwnage (http://practicalpwnage.com/blog/) wrote up a tutorial on a great Social Engineering attack. I highly recommend it.
Final Notes:
It seems like Rapid7 celebrated their victory with Metasploit Express in the Pwn-Off but also asked themselves how do I get 5/5. Looking at the features that were missing, they went back to the drawing board and the resulting product is one that truly deserves the title Professional.
Download your Free Full Featured 7-day trial at: http://www.rapid7.com/products/metasploit-pro.jsp
You can also contact Brooke Motta, Sr. Sales Director @ (857)288-7412 or by email: brooke_motta@rapid7.com
or
Jennifer Halfmann @ (857)288-7412 or by email: Jennifer_Halfmann@rapid7.com
Update: Version 3.5.1
Rapid7 released version 3.5.1 packed with lots of new features allowing Pro to strike fear in the hearts of Blue Teams.
The new Metasploit version 3.5.1 adds a lot of features to audit your network’s password security on many levels. Version 3.5.1 now downloads the configuration files of Cisco routers and extracts their passwords. The team has also added brute forcing of UNIX “r” services, such as rshell, rlogin and rexec, as well as VNC and SNMP services.
Rapid7 has added email attachments to social engineering campaigns that enable you to send out malicious PDF and MP3 files.
Metasploit now provides additional exploits for SAP BusinessObjects, Exim mail servers, ProFTPD file transfer installations, SCADA deployments (BACnet, Citect, DATAC), Novell NetWare servers, Microsoft Internet Explorer, and browser plugins such as Adobe Flash and Oracle Java.
Check out Rapid7's Blog write up about it here and the Metasploit blog here.
Tune in for a write up of all the new features and more here at n00bz.net
