Select an option from the HackMiami Pwn-Off drop down menu above
Also, please visit the AntiVirus CVE option from the menu above or click here

Metasploit Express
Setup: Running on Ubuntu, the application had a demo license that restricted the usage to 14 days. The demo license allows unrestricted scanning of IP Ranges and unlimited functionality.
Interface:
One of Core Impact Pro’s strengths is to have a simple interface and make penetration testing easy as drop, drag, pwn. Many doubted that there could be an easier way. Thank you Rapid 7 for proving the doubters wrong. (I was one of them!)
While the application runs on both Windows and your favorite Linux flavor, Metasploit Express’s console is accessed by a web browser. The interface of Metasploit Express follows the idea of KISS (Keep It Simple Stupid).
The home screen is divided into Discovery, Penetration (Bruteforce/Exploitation), Evidence Collection, and Cleanup. At the bottom of the console sits the log that keeps track of everything performed by the tool.
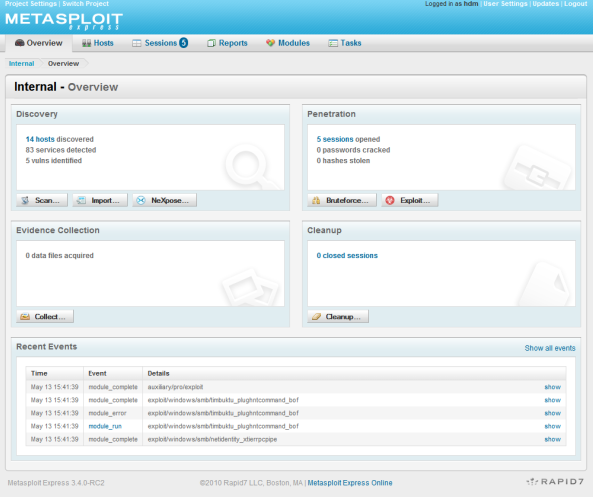
Clicking on Scan loaded the scanning engine which can be described as NMAP Powered Up (DCERPC, POP3/SMB/Postgres Fingerprinting).
The scanning engine performs port scanning as well as attempts to connect using http, SMB, SQL, telnet, and SSH among others. It was impressive to see the scanning engine did perform basic brute forcing such as identifying identical user/pass combo or no password on SMB.
Once completed, entering the hosts tab off the menu brings up the screen below. The top menu bar allows other options to be performed such as Brute force, Exploit, or Collect Evidence. Under the status, if the password was cracked or evidence looted (collected), this screen identifies the status with a colored bubble.
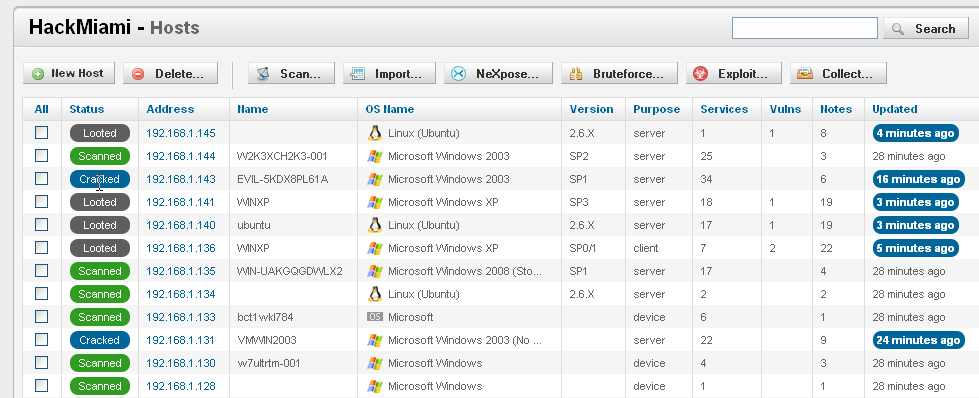
Quote from the crowd, “The interface is super clean. I am not technical and I can tell right away which machines are in trouble.”
Exploits:
Metasploit Express allows 2 options once you completed your discovery of the hosts.
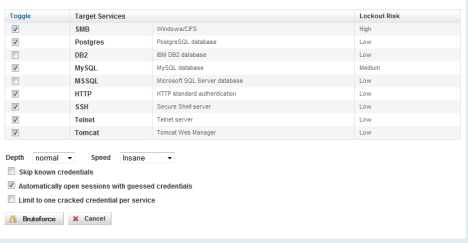
The first is brute force. Using intelligence and knowledge collected from the discovery phase, the tool attempts to break in by trying common password combinations on selected services. The tool also highlights Lockout Risk such as SMB, something I personally have done and drove the system admin’s crazy.
The other option is Exploiting. Anyone who is familiar with the Metasploit Framework is aware of this feature. This is not just autopwn. This Exploit option uses new logic and the user can selects exploits based on a rating system/stop after first shell is gained. This can minimize the chances of crashing anything. (Once again, angry admin.) There is also a dry run to see what could work without actually unleashing the exploits on the targets.
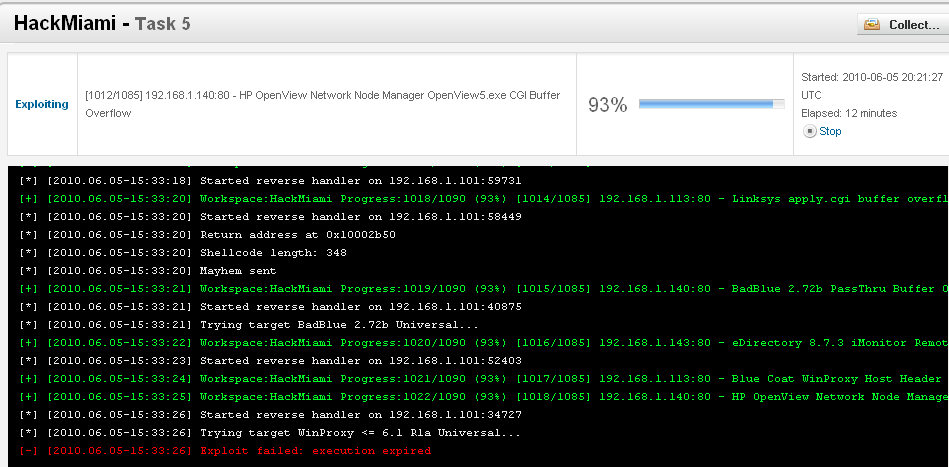
Using knowledge obtained on all processes ran up to this point, the Exploiting task unleashes pwn-ership on the targets.
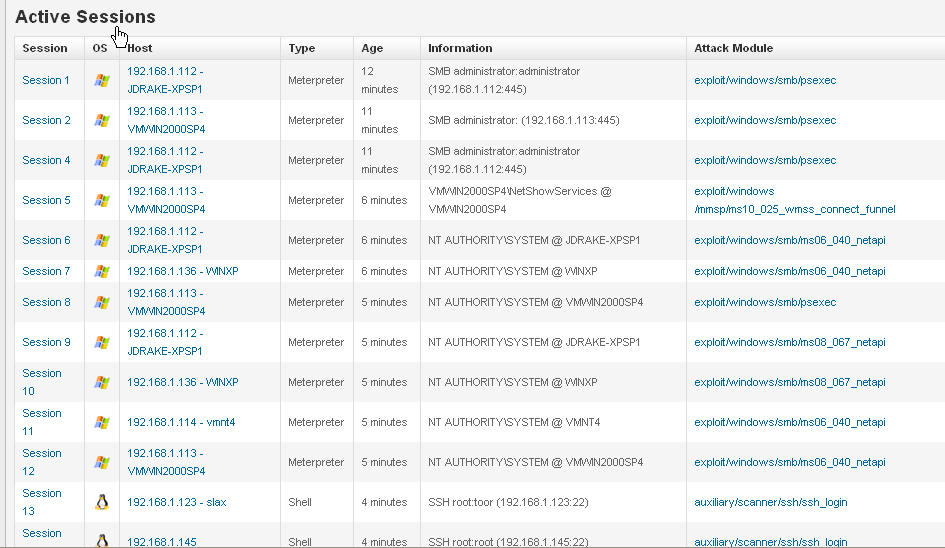
Using the web front end to generate the list of sessions spawned, I wondered how the shell interaction would play out. Metasploit Express wowed many when the tool generated both a Windows Shell (by connecting to a VNC service connected to a meterpreter) and a Unix Shell all within the browser.
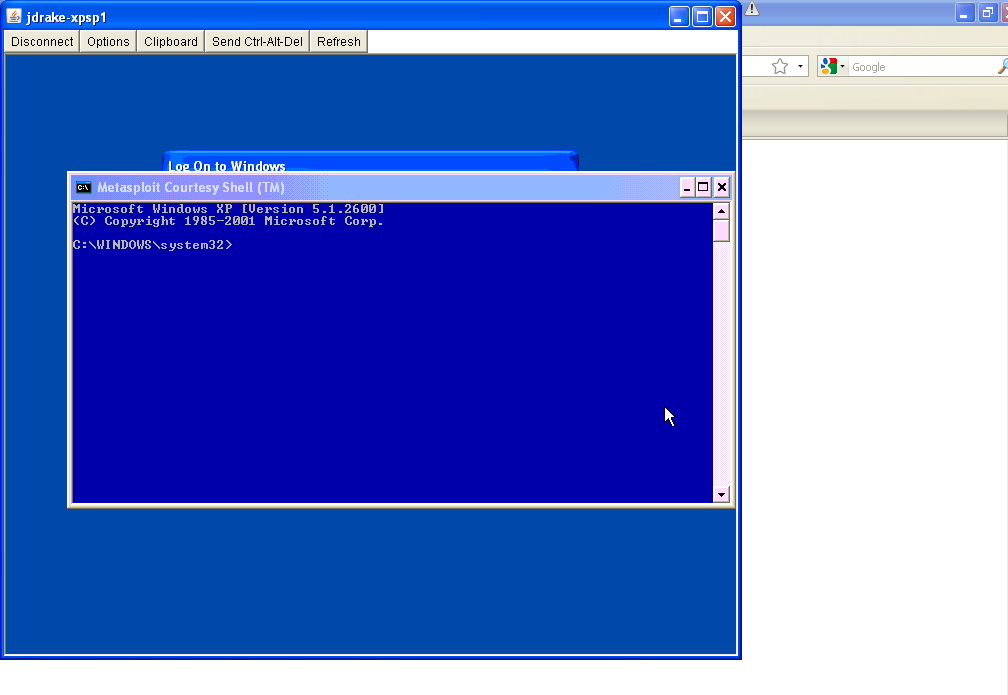
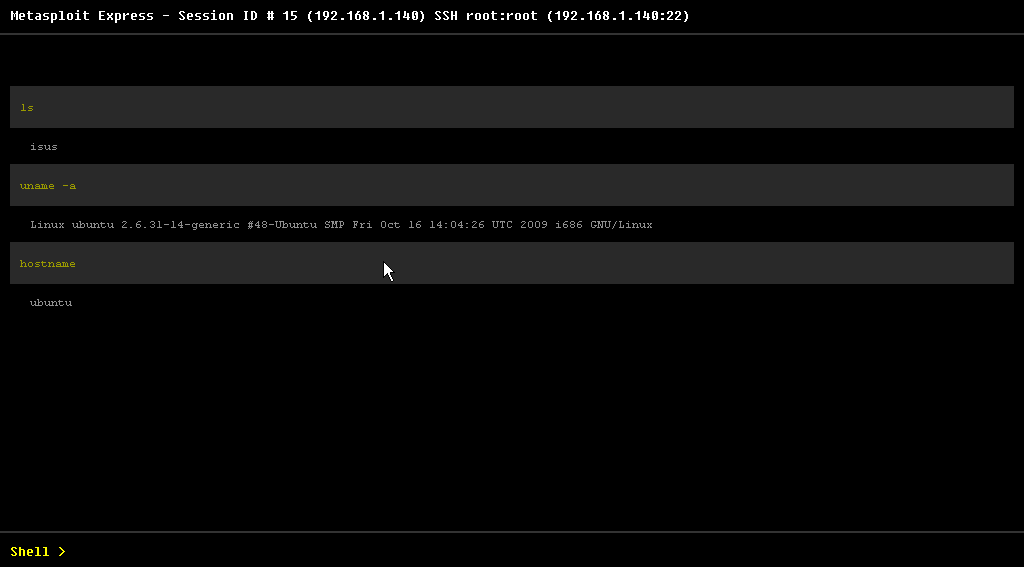
Total number of exploits found: 16 shells across EIGHT boxes
Quote from the crowd, “The tool was able to gain in only a few minutes 16 shells at target machines (one of them was a VM I provided).”
Quote from the crowd,”Good bye drop, drag, pwn. Hello point, click pwn.”
Reporting:
Before we get into the reporting aspect of Metasploit we need to understand what goes into the report that the decision makers want to see. “Server blah blah has a blah blah which could be blah.”
A good penetration test report delivers not risks to the servers, but illustrates the risk more than a number 0.0-10.0. When I receive an audit report, the first thing I do is challenge the report. Maybe it is a defensive method a la Dr. Freud. One think you can’t argue against is evidence. (However, that still doesn’t stop me personally from trying.)
One of the tasks I hate the most when performing penetration testing is collecting evidence.
Once a machine has been exploited, Metasploit Express provides a function every penetration tester and auditor will love. All one needs to do is click the Collect button and the machine is “Looted.”
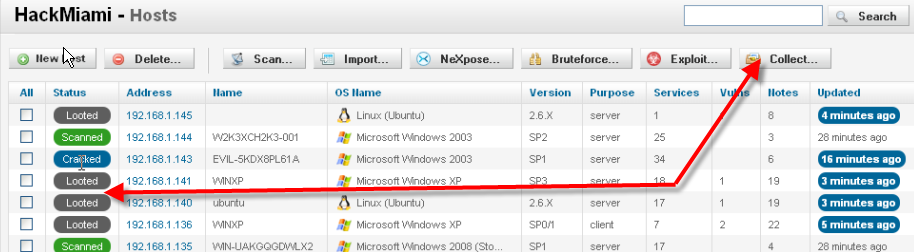
Among the goodies collected by Metasploit Express are:
RSA keys (both public and private)
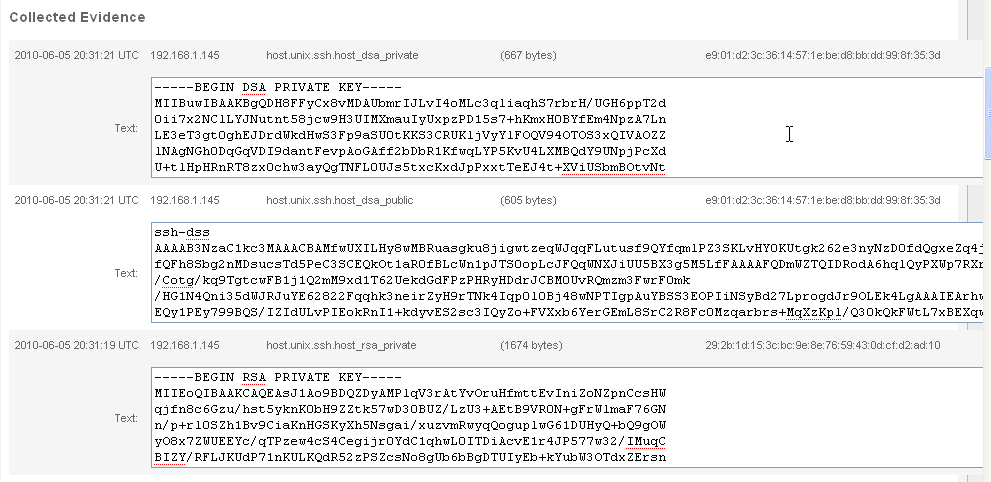
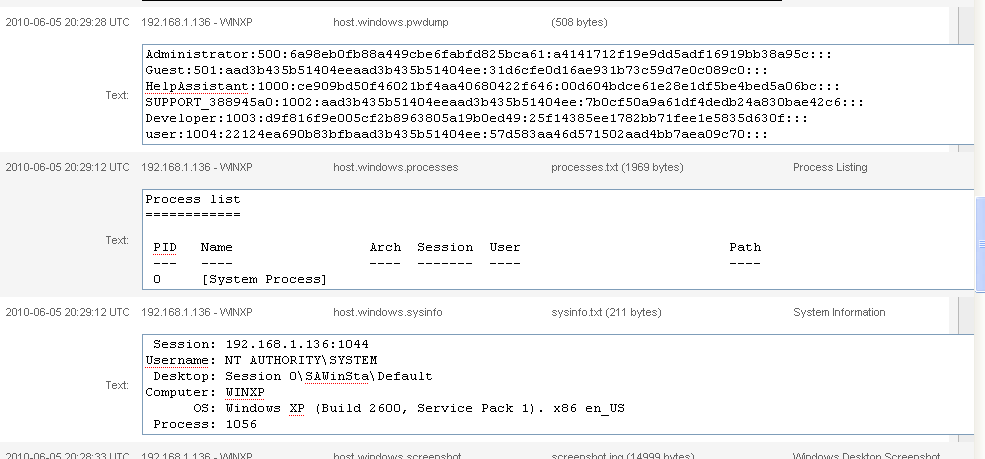
Windows SAM file, Windows Processes, Windows Sysinfo
A screen shot of what is on the monitor at the time.
Getting all that information out of the tool is just as easy as obtaining the information.
Clicking on Report will allow you to run several ad-hoc reports in PDF, Word, XML, and a full dump in a zip file. You can mask username/passwords when generating the reports.
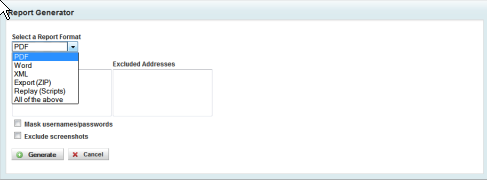
One of my favorite reporting options is the Replay Scripts. The Replay Script will allow someone to download the Framework and Replay the attack without requiring the Express Product.
Click here to download the replay for 192.168.1.113- A Windows NT
exploited using exploit/windows/smb/ms06_040_netapi
As a Sr. Manager from a Big 4 Public Accounting Firm said, “It is 2010 and I can’t believe this feature is only making it to the market now. By allowing a client to retest a finding will allow them to remediate and retest, this will save time on our part and consultant fees on their part. By providing the option to replay the attack, we can provide our clients value above and beyond just a report.”
Value and Additional Features:
Metasploit Express cost $3000. It is the cheapest in price of our tools in the test; however the cheap price does not mean a lower quality tool by any means.
The name of the product is misleading. When one thinks of the work express, one thinks that it is lacking or scaled down. This could not be further from the truth. As it was observed from the demo, express was the speed that it pwned machines saving the tester valuable time which is money.
Included with the purchase of Metasploit Express is full support by Rapid7 security and support specialists in addition to the large and growing Metasploit community.
This is the first commercial release of the Metasploit project and the team at Rapid 7 has set the bar up very high. The rumor mill is to be on the lookout for a professional version with even more features packed into it. Look out vulnerable machines and competitors alike.
For more information and to get a trial of Metasploit Express,
Contact Brooke Motta, Sr. Sales Director @ (857)288-7412 or by email: brooke_motta@rapid7.com
The Scorecard
Interface: The interface is super clean compared to the other applications. Metasploit Express uses a web browser to interact with the application. It doesn't matter what OS you are used to, if you have ever surfed the web, you can "Point, Click, Pwn!"
Exploits: Metasploit Express Generated 16 shells across EIGHT boxes. The speed at which the targets fell justified the name "express."
Reporting: With a single click, the evidence collection feature does the dirty work of collecting evidence from the targets. This feeds into the reporting feature of the tool. The reports generated out of Metasploit Express include the evidence collected which includes user/password combinations, encryption keys and screen shots of the target machine. In this case, a picture is worth a thousand words.
Value: Metasploit Express was the most affordable with a list price of $3,000.
Additional Features: A favorite feature of Metasploit Express is the Replay Scripts. By enabling one to replay the attack without requiring the Express Product,a tester would be able to provide value above and beyond just a report.
Total Score:
