Select an option from the HackMiami Pwn-Off drop down menu above
Also, please visit the AntiVirus CVE option from the menu above or click here
Setup: Running on Windows XP Professional, the application had a demo license that restricted the IP range that was able to be scanned from 192.168.1.100 through 192.168.1.120. The IP restriction did cause disadvantages in the test as only 20 machines from the many we had were able to be scanned.
Interface:
Core Impact PRO is a desktop application. The interface is one that is familiar to the Windows User. Loading the Workspace, the user is required to enter an 8 character password. This protects the data uncovered during the scan. According to the company, “It is important that we detect the vulnerabilities and not create new ones.”
The side menu looks familiar if you have ever used Outlook with 3 tabs on the side, Network RPT, Client Side RPT, and Web Applications RPT.
The Network RPT menu offered steps needed to perform a penetration test.
Clicking on “1. Network Information Gathering “ the network discovery process started and shortly our hosts arrived.
Quote from the crowd, “The interface is very intuitive and self explanatory.”
Exploits:
Clicking of “2 Network Attack and Penetration” unleashed the exploits mapped to the information identified in step 1. During the test, we did not specify which exploit but rather use the knowledge obtained in the Information Gathering Stage (OS Detection, Open Ports, etc.) to select the exploits that matched the target machines and unleash all the exploits in its bag of tricks.
Once the machine was exploited, Core deployed their agents. The agents are memory resident and according to the company “not detected by major AV products.”
From the agent, one can perform all sorts of “fun” things such as grab the password hashes, upload and download files, or my favorite which is to obtain a shell.
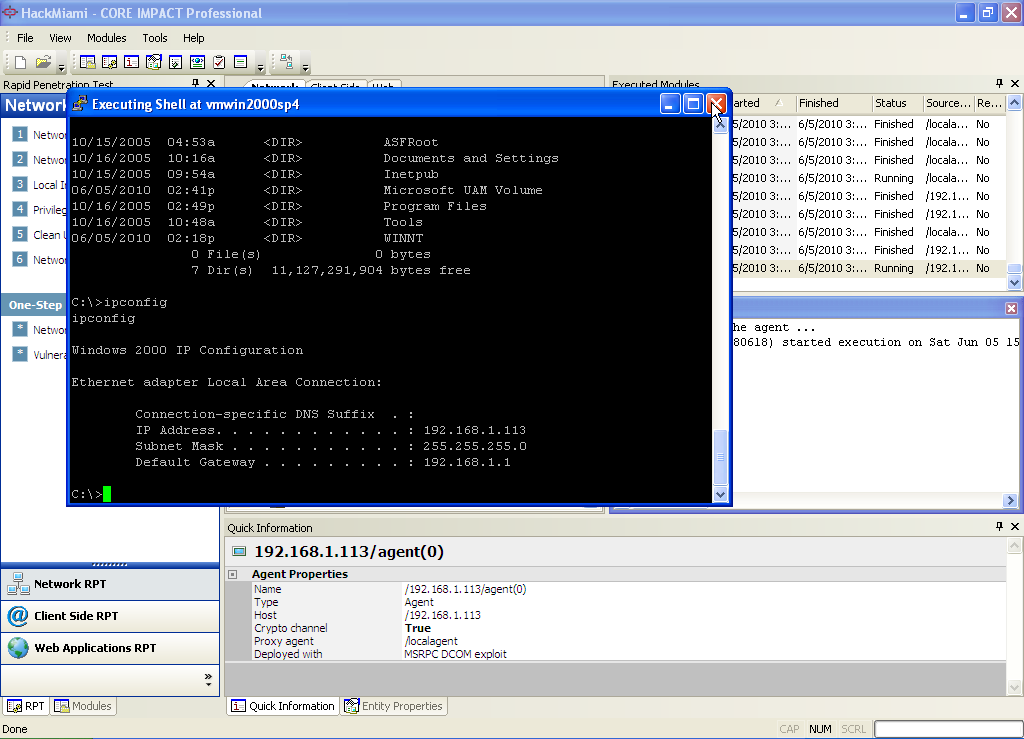
The agents as noted before are secure sessions that tie back to the protected workspace that originated the attack. We want to discover problems, not create new ones.
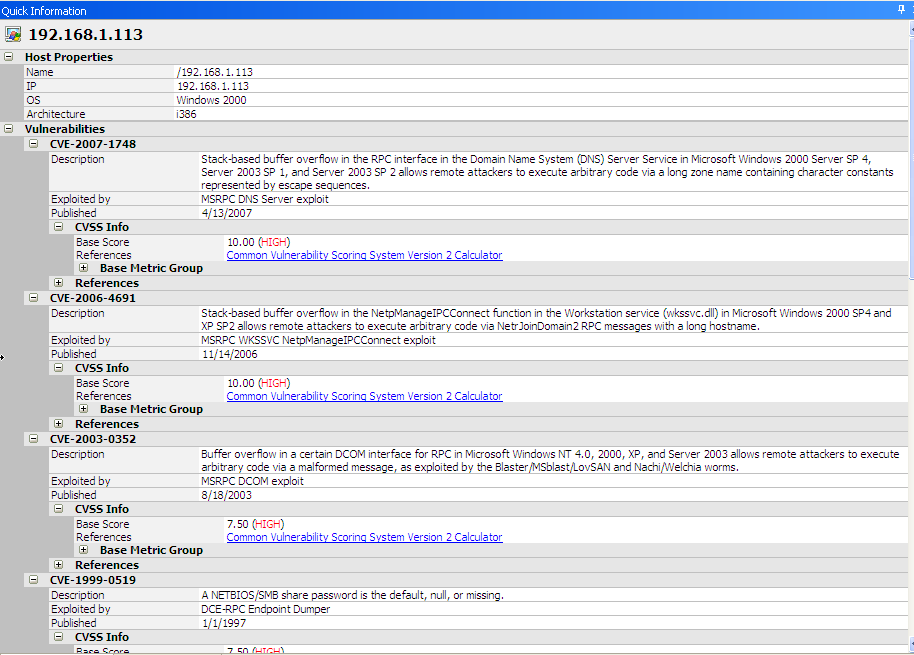
Total number of exploits found: 4 unique exploits and generated 3 shells.
When exploiting, Core Impact did detect Metasploit Framework on my computer and offered for run autopwn against the targets. During the test, this option was not ran as Metasploit Express was in the contest. We did not test the integration of the Core Impact and the Metasploit Framework.
In theory, Core might have identified the same ones Metasploit would have identified.
http://blog.coresecurity.com/2010/02/16/integrating-core-impact-pro-with-metasploit/
However, in the real world, an attacker would do what it takes to get through the security and in a penetration test, so should the tester.
Quote from the crowd, "It took this product way less time [compared to Canvas] to gain shell in one of the machines.”
Reporting:
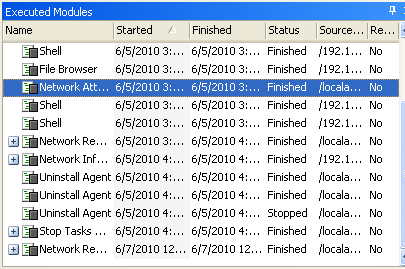
Once a machine has been exploited, Core Impact PRO will collect data and add it to the knowledge collected on the target. The last step in all of Core Impact’s step by step processes is reporting. All the products save a history of all tasks performed and Core is no different. Below is a screen shot of the log file of all modules executed and the status.
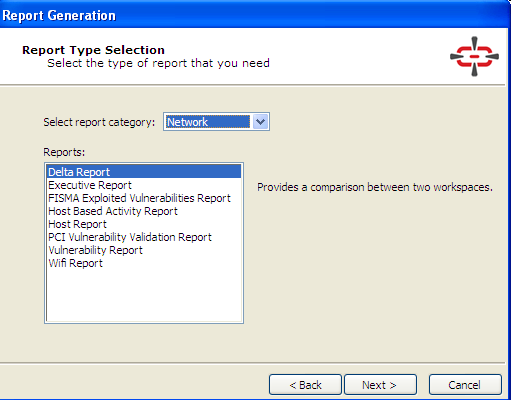
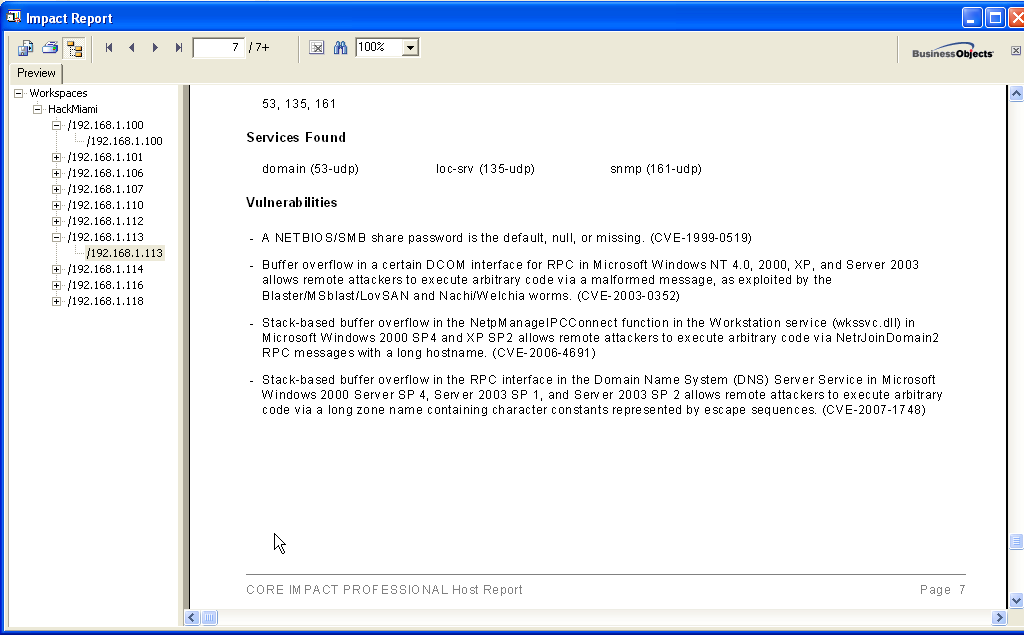
The tool offers several options in Report Generation. The reports can be fully customized and generated in Word, PDF, and XML formats.
Value and Additional Features:
Core Impact Pro has a pricing range from $30,000 through $60,000. The lower end of the scale will restrict the number of IP addresses one could scan while the high end of the scale removes those restrictions.
This price of Core Impact Pro is not cheap price by any means. With Core Impact Pro, you get what you pay for; in this case, everything even rumored the kitchen sink in a future version.
While this test only focused on the network remote exploitations of the application, there is much more under the hood.
As many will tell you, the number one risk in computer security is located at the keyboard. 10 years ago, phishing was a term I used to go to a concert and listen to some jam music and have a really good time. Now it is in the front of the news on a regular basis. Users are going to web sites that host nasty bugs, giving too much information away on Facebook or Linked In, and opening every attachment sent to your inbox (DAD, THIS MEANS YOU)!
Core Impact Pro helps perform and manage a test of the security awareness of your users. By generating emails and sending them to the list of addresses you define or discover, the tool will create, administer and report the results of a social engineering test.
This is an attack vector that can create unlimited holes in the concrete security of a company.
We can’t forget about the 3rd attacking option, Web Applications Testing.
SQL injections, PHP shells and XSS… the world maybe getting smaller but the number of web security issues is not. Everyone in this day and age has a presence on the web. People’s dogs and teddy bears have Facebook pages. With added complexity to the web 2.0/3.0, new attack vectors are being discovered every day. Core Impact allows you to discover them for yourselves before the attackers do.
For pricing information and to get a trial of Core Impact Pro,
Contact Lissa Gelbwachs, Southeast Account Manager @ (617)695-1167 or by email: lgelbwachs@coresecurity.com
The Scorecard
Interface: The interface is familiar to Windows Users. Drag, Drop, Pwn
Exploits: Core launched 3 agents/shells with ease. It may have found more using the Metasploit plug-in.
Reporting: The reports generated out of the application were easy to read and informative. They did seem plain however.
Value: Core topped the price list of our competitors. If money was no option, I would buy all 3, however usually it does factor into the equation.
Additional Features: With a higher price, Core is packed with additional features. Core includes not only Network Testing, but Web and Client Side/Phishing attack vectors as well. You will pay for these features however.
Total Score:

